Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
Search Results For - Protocols
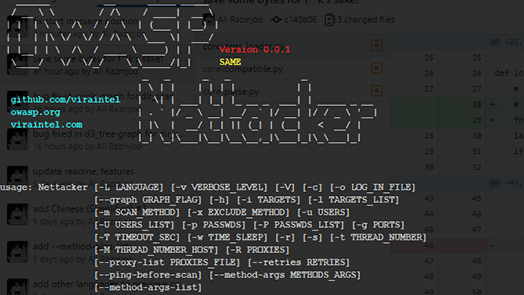
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
SDRtrunk is an integrated application for demodulating radio signals and decoding trunked radio network protocols and some related radio signal formats. The...
Microsoft is addressing unusual of the performance subdividing for fixing patches to relieve the Meltdown and Spectre vulnerabilities. Windows Chief Terry...
Youbit is a South Korean exchange that got hacked last week. As per reports, it is believed that around one-fifth of the clients’ holdings were stolen by...
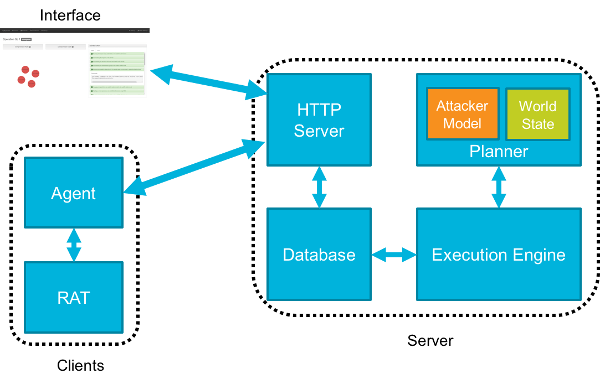
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
Features Auto VoIP/UC penetration test Report generation Performance RFC compliant SIP TLS and IPv6 support SIP over websockets (and WSS) support (RFC 7118)...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...