Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...
Search Results For - Protocols
Sn1per Community Edition is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Sn1per...
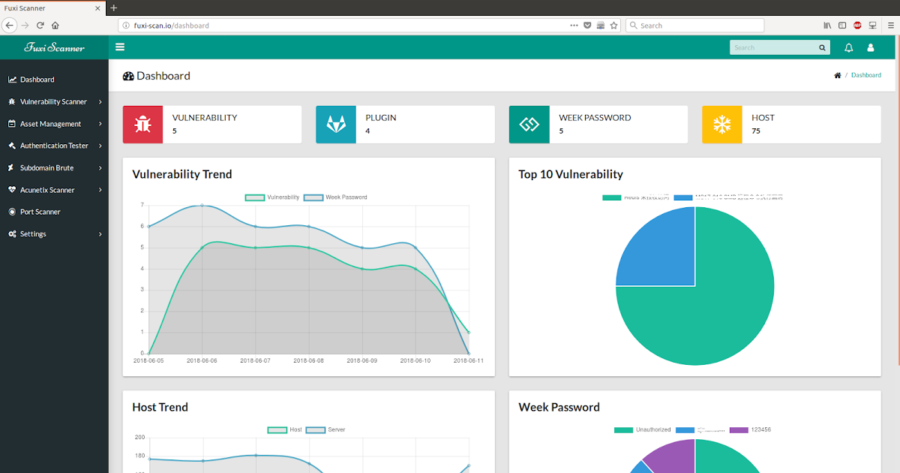
Fuxi Scanner is an open source network security vulnerability scanner, it comes with multiple functions. Vulnerability detection & management...
Deplug is a graphical network analyzer powered by web technologies. Features Cross-Platform (macOS, Linux, Windows) Web-based UI (Electron) Built-in Package...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
Sn1per is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Features: Automatically collects basic...
FIDO U2F Security key is a personal encryption method which individualizes your online security by providing a secondary layer of encryption via the USB port...
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP) for the...
mitmproxy is your swiss-army knife for debugging, testing, privacy measurements, and penetration testing. It can be used to intercept, inspect, modify and...
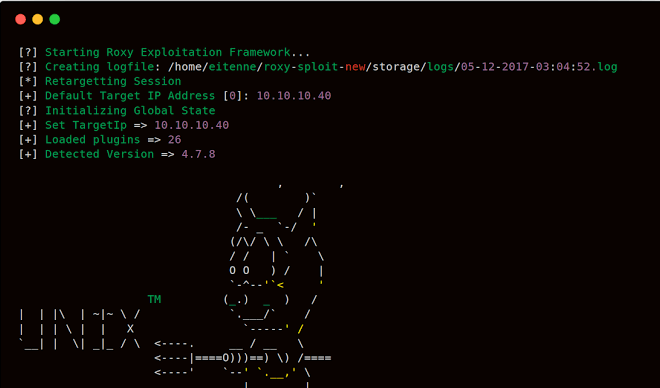
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...