A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
Search Results For - PRETty
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
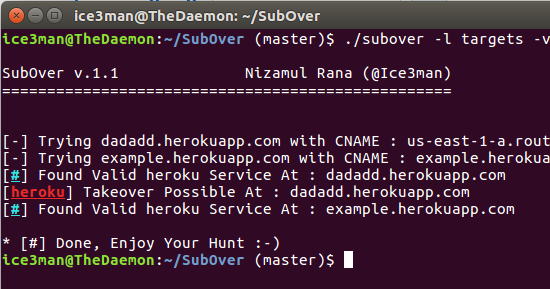
[sc name=”ad_1″] Subover is a Hostile Subdomain Takeover tool originally written in python but rewritten from scratch in Golang. Since it’s...
Author: Marshall Taylor Blockchains and their cryptocurrencies are energetically following a path similar to other major leaps in technology that have come...
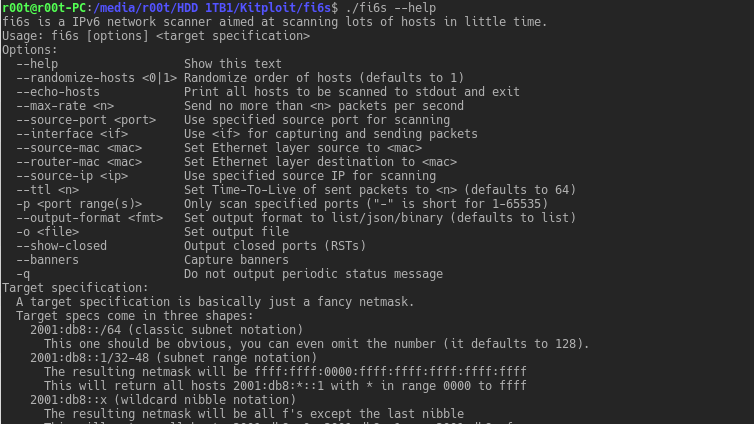
fi6s is a IPv6 port scanner designed to be fast. This is achieved by sending and processing raw packets asynchronously. The design and goal is pretty similar...
One of the biggest stories of the year so far has been the scandal surrounding Cambridge Analytica that came out after a Channel 4 expose that demonstrated the...
Author: Alex Moskov What is Litecoin? Litecoin (LTC) is a decentralized peer-to-peer cryptocurrency that was released on October 7th, 2011 and went live on...
Hardentools is a collection of simple utilities designed to disable a number of “features” exposed by operating systems (Microsoft Windows, for now), and...
It’s time to learn how to renew its OS because researcher James Bercegay has found a dozen models possess a hard-coded backdoor. The backdoor, lets anyone log...
“This is the start of a long legal battle. Netflix stands w/ innovators, large & small, to oppose this confused FCC order,” the company tweeted quickly...