[sc name=”ad_1″] You’ve got a lot of maps and they are getting pretty unruly. What do you do? You put them in a book and call it an atlas...
Search Results For - PRETty
[sc name=”ad_1″] SGN is a polymorphic binary encoder for offensive security purposes such as generating statically undetecable binary payloads. It...
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right...
[sc name=”ad_1″] Impost3r is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C. Attackers can use Impost3r...
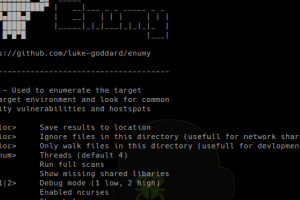
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
[sc name=”ad_1″] Shellerator is a simple command-line tool aimed to help pentesters quickly generate one-liner reverse/bind shells in multiple...
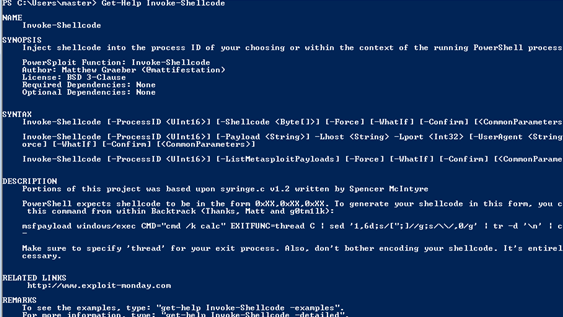
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
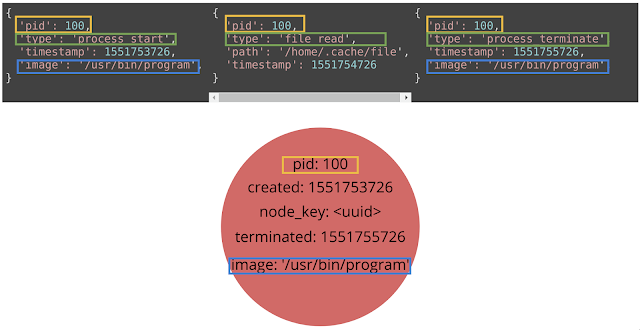
[sc name=”ad_1″] Grapl is an open source platform for Detection and Response (D&R). The position that Grapl takes is that Graphs provide a more...
[sc name=”ad_1″] Exclusive — A security researcher has identified an unsecured server that was leaking detailed personal details of nearly half a...
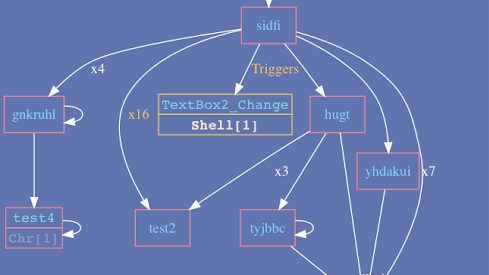
A tool for security researchers, who waste their time analyzing malicious Office macros. Generates a VBA call graph, with potential malicious keywords...