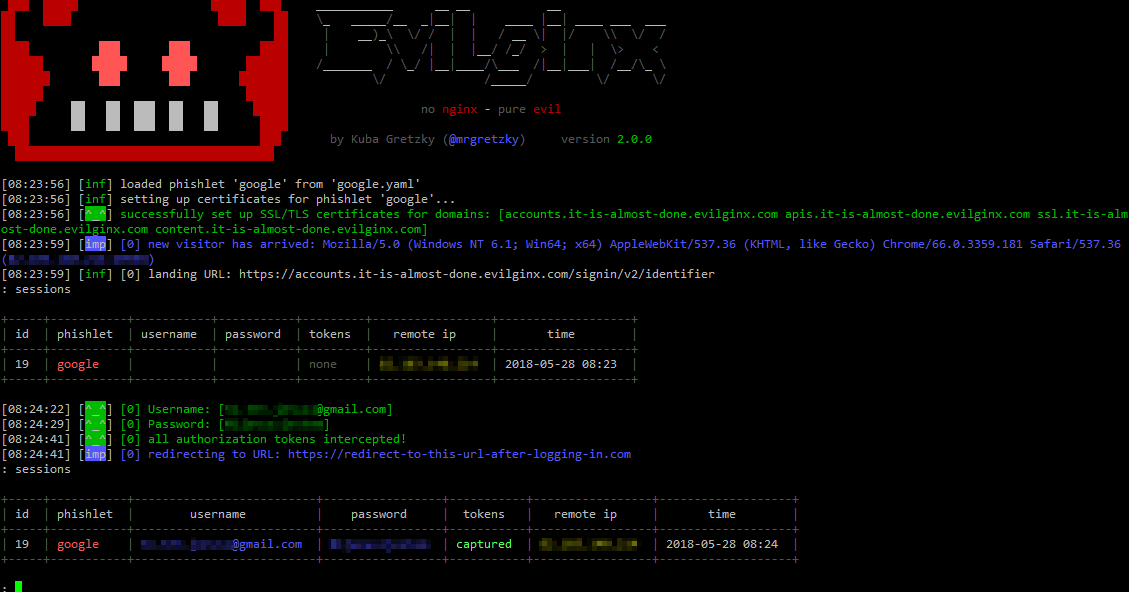
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor...
Search Results For - Binary
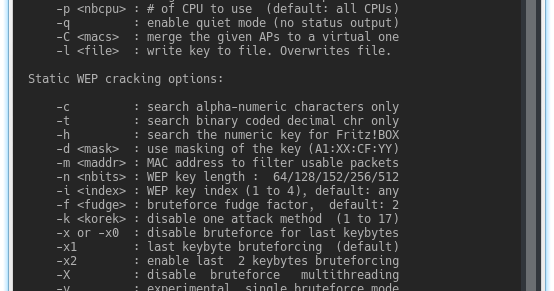
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
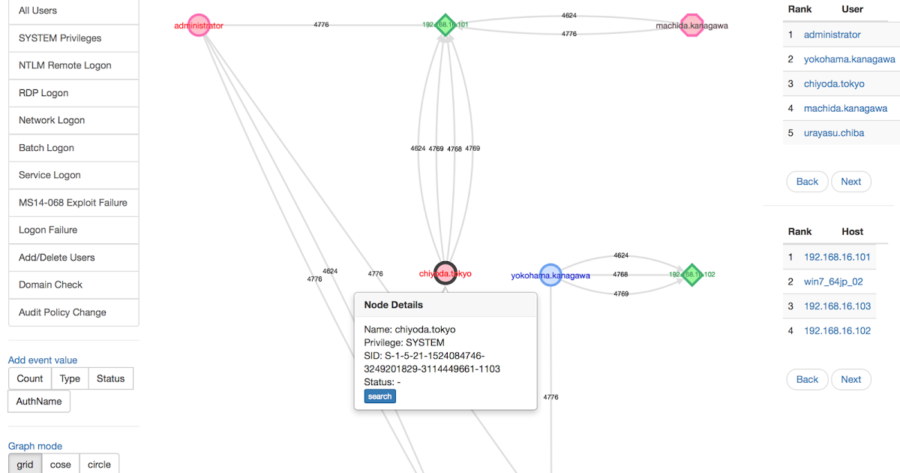
Investigate malicious logon by visualizing and analyzing Windows active directory event logs. Concept LogonTracer associates a host name (or an IP address) and...
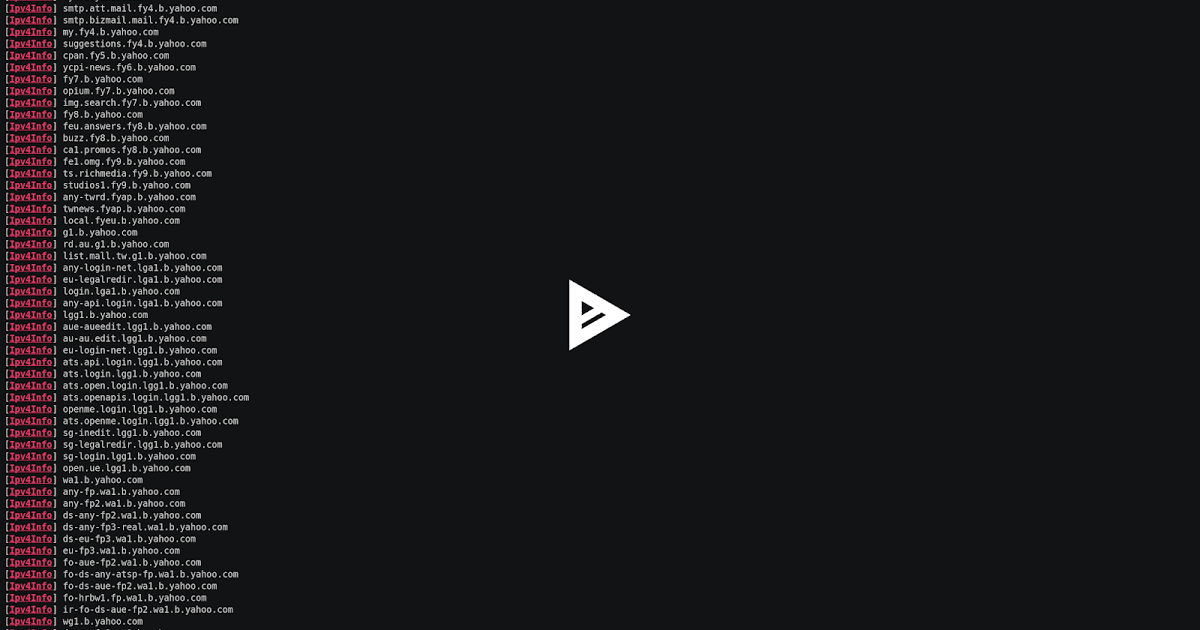
SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
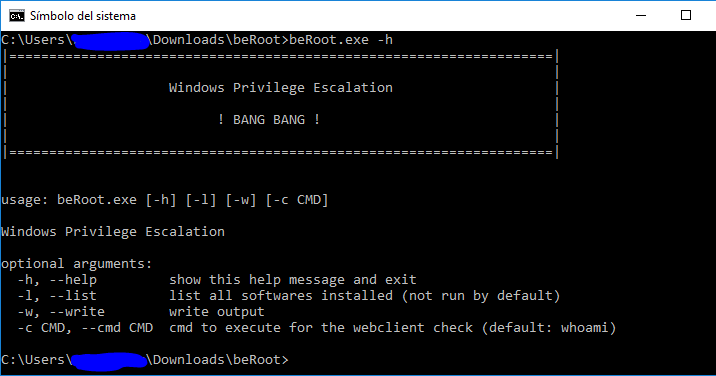
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
Airbash is a POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. It is compatible with Bash and Android Shell...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some...
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...