[sc name=”ad_1″] An extensible application for penetration testers and software developers to decode/encode data into various formats. Setup...
Tag - SHA1
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...
[sc name=”ad_1″] PwnedPasswordsChecker is a tool that checks if the hash of a known password (in SHA1 or NTLM format) is present in the list of I...
[sc name=”ad_1″] Mihari is a helper to run queries & manage results continuously. Mihari can be used for C2, landing page and phishing hunting...
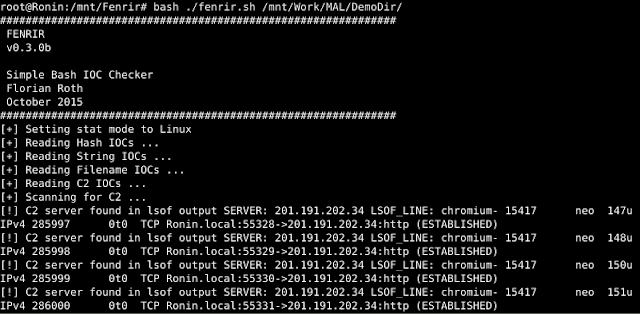
[sc name=”ad_1″] Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise...
[sc name=”ad_1″] Mitaka is a browser extension for OSINT search which can: Extract & refang IoC from a selected block of text. E.g. example[...
Hash Buster is a program which uses several APIs to perform hash lookups. Features Automatic hash type identification Supports MD5, SHA1, SHA2 Can extract...
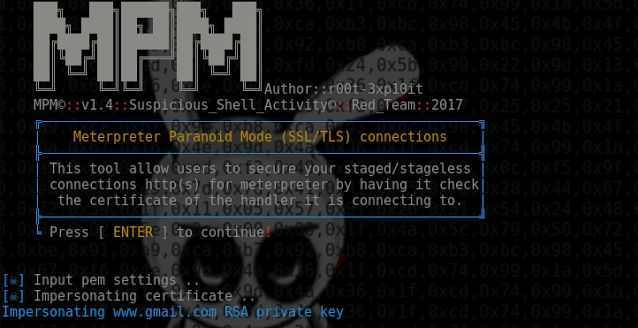
Meterpreter_Paranoid_Mode.sh allows users to secure your staged/stageless connection for Meterpreter by having it check the certificate of the handler it is...
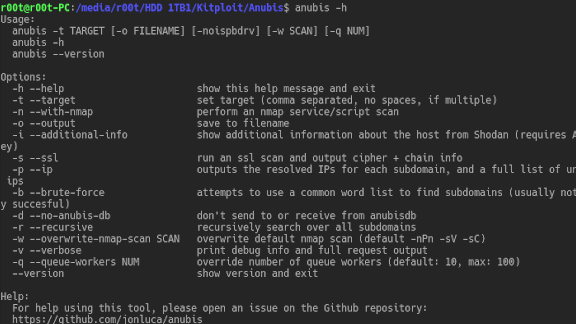
Anubis is a subdomain enumeration and information gathering tool. Anubis collates data from a variety of sources, including HackerTarget, DNSDumpster, x509...