Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
Search Results For - Remote
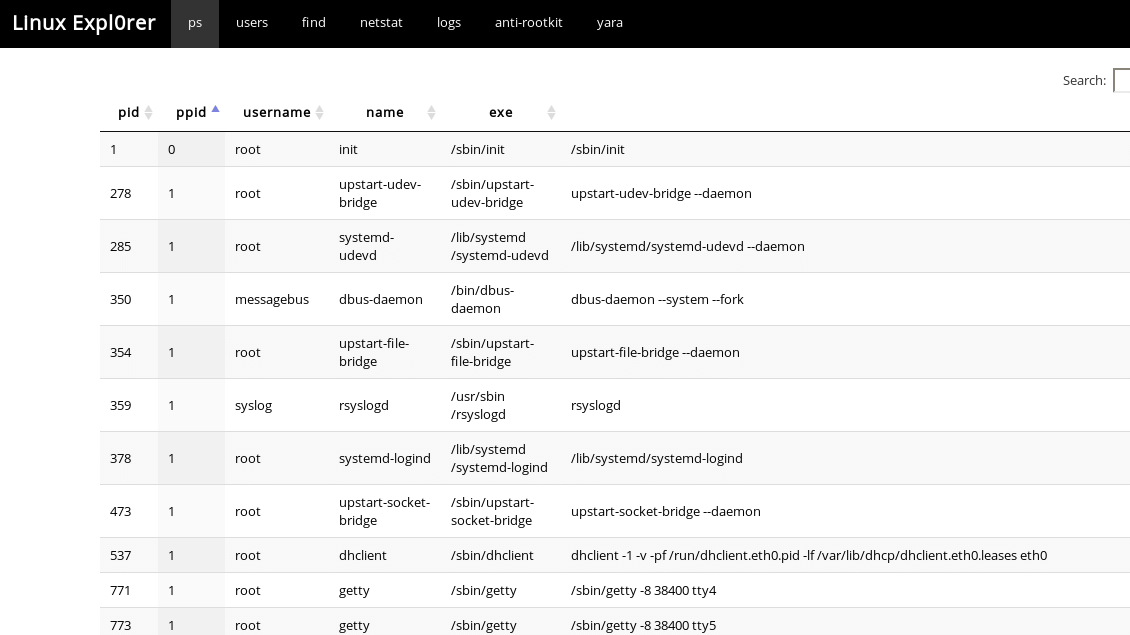
Easy-to-use live forensics toolbox for Linux endpoints written in Python & Flask. Capabilities ps View full process list Inspect process memory map &...
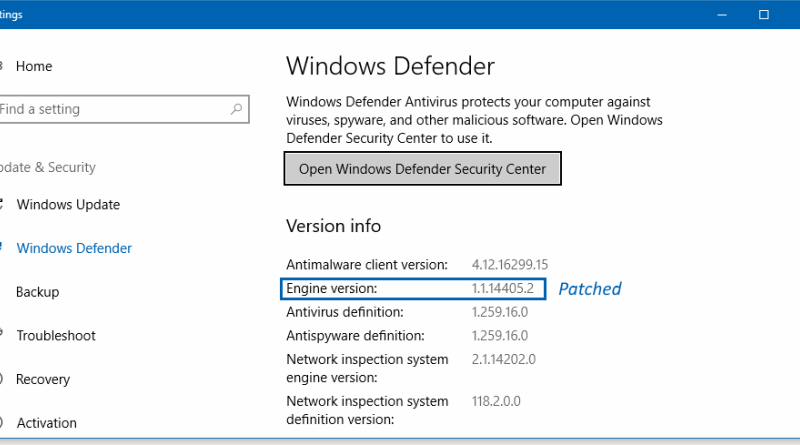
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...
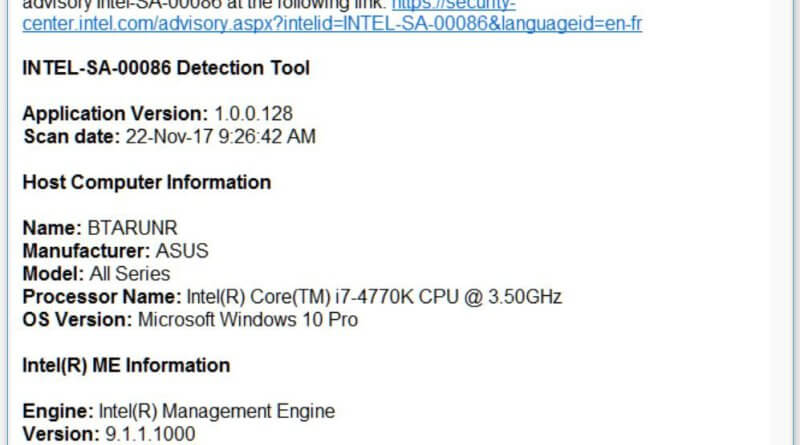
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
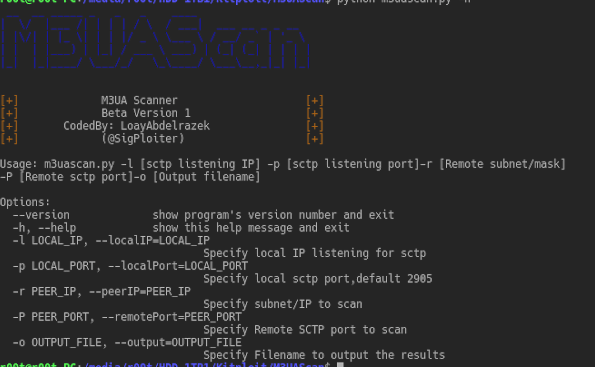
A Scanner for M3UA protocol to detect Sigtran supporting nodes M3UA stands for MTP Level 3 (MTP3) User Adaptation Layer as defined by the IETF SIGTRAN working...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
What this tool does is taking a file (any type of file), encrypt it, and embed it into an HTML file as ressource, along with an automatic download routine...
Excalibur is an Eternalblue exploit based “Powershell” for the Bashbunny project. It’s purpose is to reflect on how a “simple”...
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...