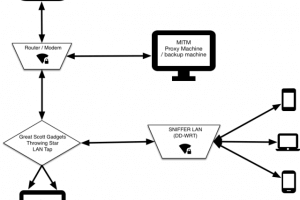
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
Search Results For - Remote
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
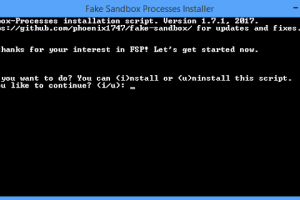
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software...
The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
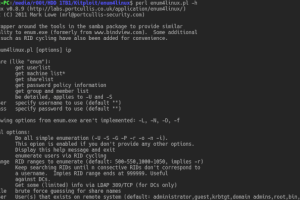
A Linux alternative to enum.exe for enumerating data from Windows and Samba hosts. Enum4linux is a tool for enumerating information from Windows and Samba...
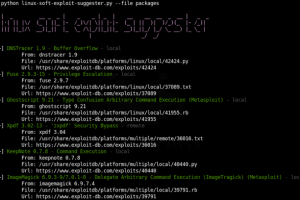
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
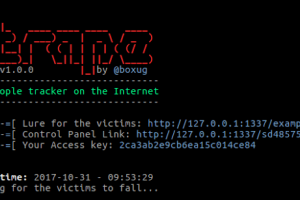
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...