As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
Search Results For - Remote
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
Simple TCP reverse shell written in Go. It uses TLS to secure the communications, and provide a certificate public key fingerprint pinning feature, preventing...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
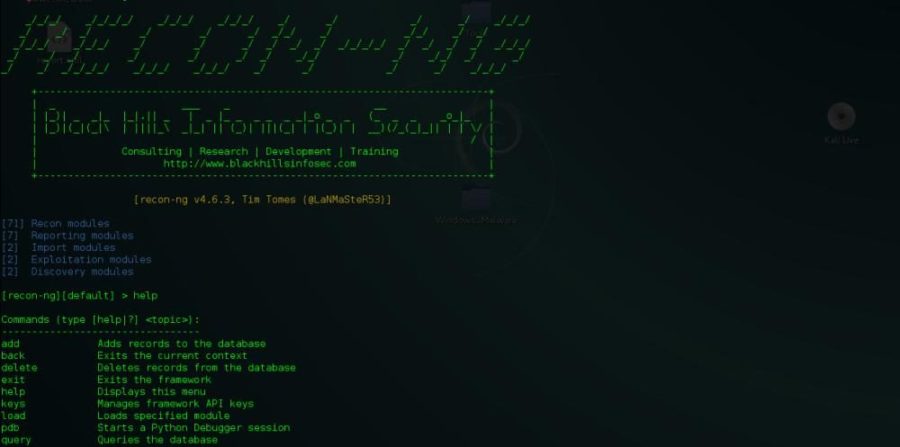
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience...
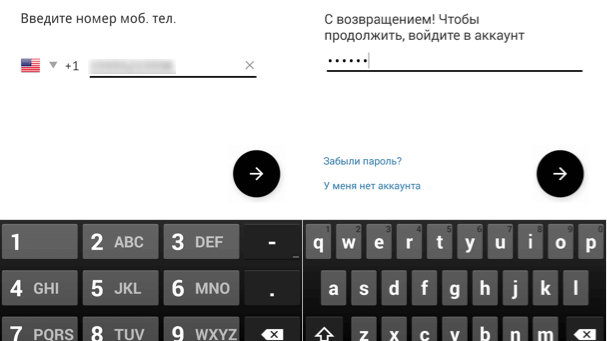
Millions of people have become victims of a FakeApp that is using new tricks to cheat Uber users around the world. Security researchers from Symantec...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
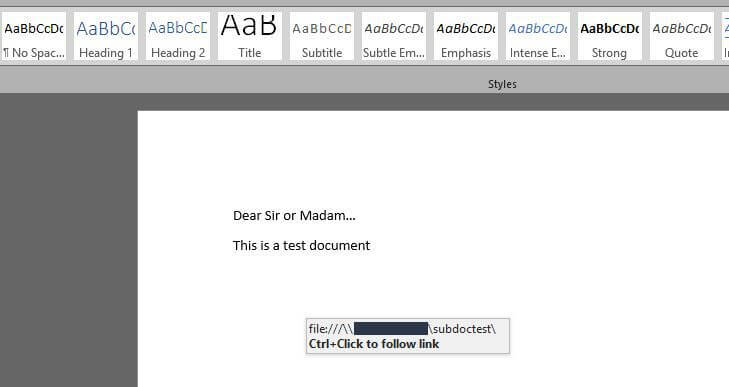
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
A Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems. What do I need to run it...