These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to remotely run machines, even when the device is not booted. Let me repeat that: If your PC has power, even if it’s not going, it can be attacked. If an attacker happily exploits these holes, the attacker can run malware that’s totally transparent to the operating system.
Most, but not all, of ME’s vulnerabilities, require mechanical access for someone to exploit. Another would valid requite managing credential for remote exploitation. Still, it’s worrisome.
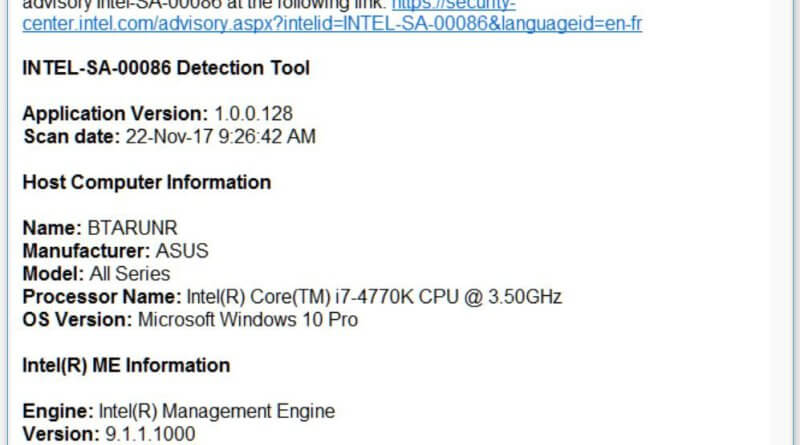
Intel has published a detection tool so Linux and Windows users can detect if their machine is vulnerable. The organization also has a page that provides links to support pages from each vendor, as they confirm vulnerable machines.
Intel has confirmed that the following CPUs are vulnerable:
- 6th, 7th, and 8th generation Intel Core Processor Family
- Intel Xeon Processor E3-1200 v5 and v6 Product Family
- Intel Xeon Processor Scalable Family
- Intel Xeon Processor W Family
- Intel Atom C3000 Processor Family
- Apollo Lake Intel Atom Processor E3900 series
- Apollo Lake Intel Pentium Processors
- Intel Celeron G, N, and J series Processors
There are firmware applications either available now or on the way for most of these chips. The transmission of these patches is in the hands of hardware vendors.
There is, of course, also the opportunity of more security holes being discovered in these chips. That’s why some vendors are walking away from Intel ME.
First, the well-important Linux PC maker System76 announced it was publishing an open-source program to “automatically deliver firmware to System76 laptops similar to the way software is currently distributed through the operating system.” This schedule will “automatically deliver updated firmware with a disabled ME on Intel 6th, 7th, and 8th Gen laptops.”




















Add Comment