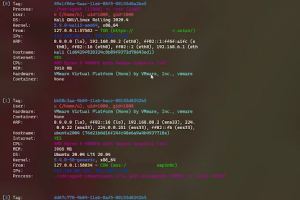
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
Search Results For - Exploitation
[sc name=”ad_1″] Sploit is a Go package that aids in binary analysis and exploitation. The motivating factor behind the development of sploit is to...
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
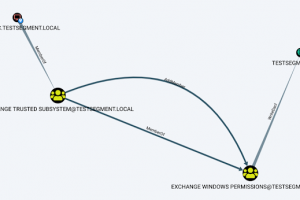
[sc name=”ad_1″] Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a...
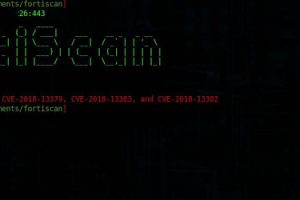
[sc name=”ad_1″] (CVE-2018-13379) Exploitation Tool, You can use this tool to check the vulnerability in your FortiGate SSL-VPN. ...
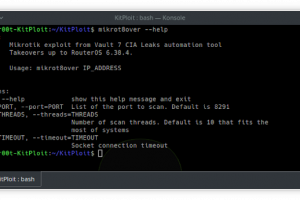
[sc name=”ad_1″] mikrot8over: Fast exploitation tool for Mikrotik RouterOS up to 6.38.4 This is reworked original Mikrotik Exploit. Added Python 2...
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
[sc name=”ad_1″] DeimosC2 is a post-exploitation Command & Control (C2) tool that leverages multiple communication methods in order to control...
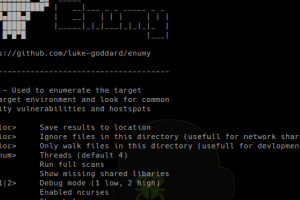
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
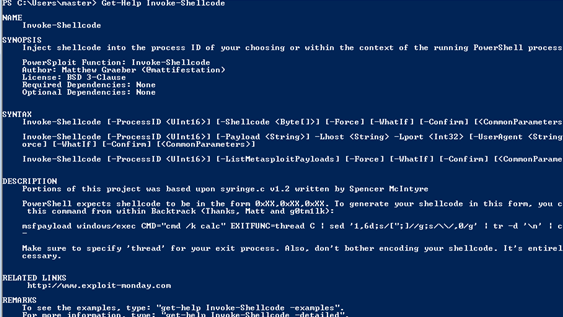
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...