[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
Search Results For - Exploitation
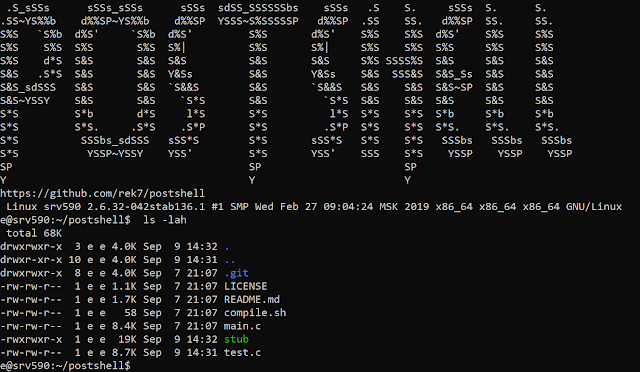
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
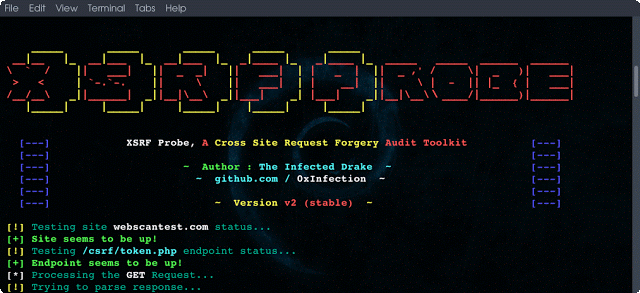
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
Pacu is an open source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security...
Bashark aids pentesters and security researchers during the post-exploitation phase of security audits. Usage To launch Bashark on compromised host, simply...
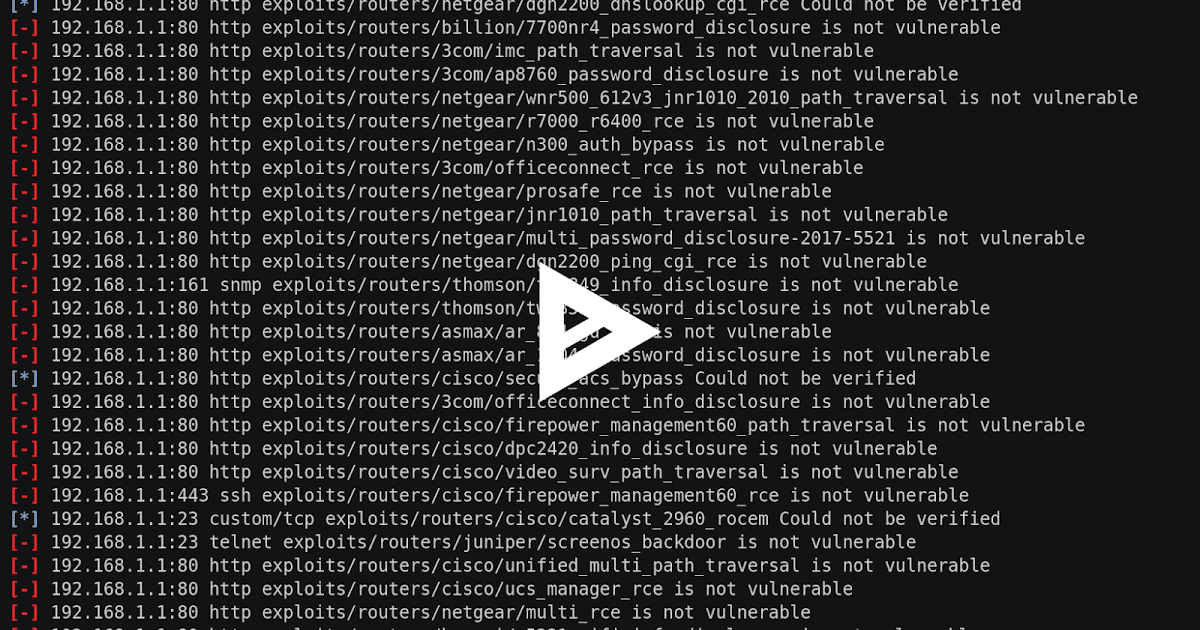
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
XSStrike is an advanced XSS detection and exploitation suite. It has a powerful fuzzing engine and provides zero false positive result using fuzzy matching...
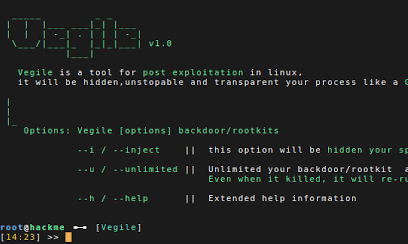
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...