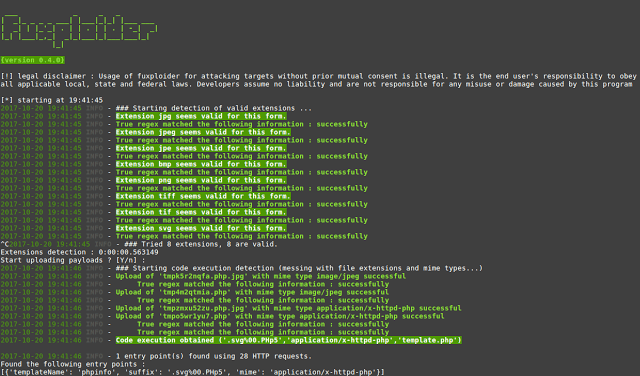
fuxploider is an open source penetration testing tool that automates the process of detecting and exploiting file upload forms flaws. This tool is able to...
Search Results For - Exploitation
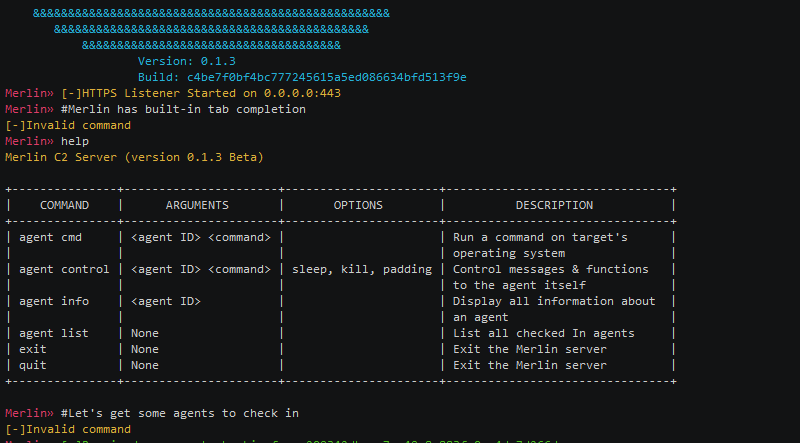
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
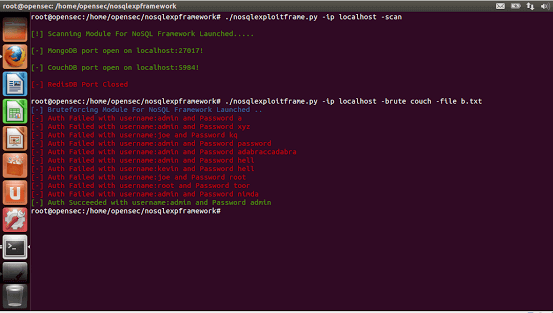
A FrameWork For NoSQL Scanning and Exploitation Framework Authored By Francis Alexander. Added Features: First Ever Tool With Added Support For...
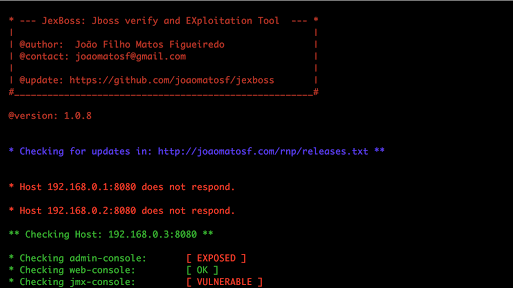
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc. Requirements...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
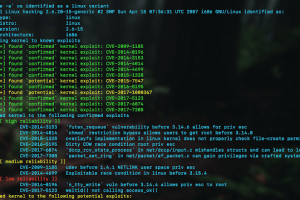
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...
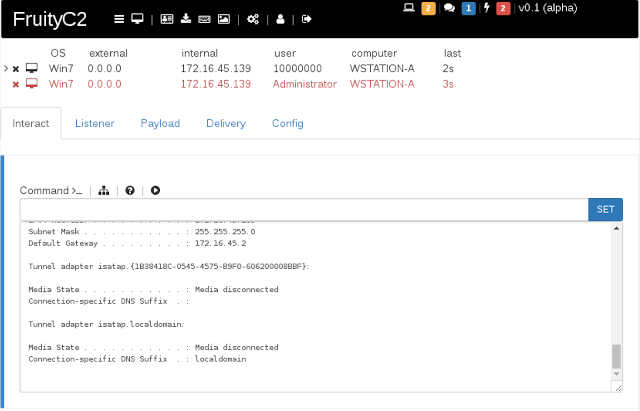
This is the initial release for FruityC2 (alpha version). Can be installed on any linux system, but the installation scripts are made for Debian based systems...
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
[sc name=”ad_1″] HyperDbg is designed with a focus on using modern hardware technologies to provide new features to the reverse engineering world...
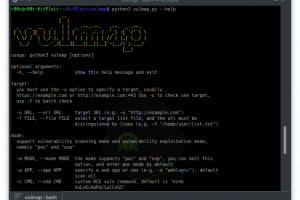
[sc name=”ad_1″] Vulmap is a vulnerability scanning tool that can scan for vulnerabilities in Web containers, Web servers, Web middleware, and CMS...