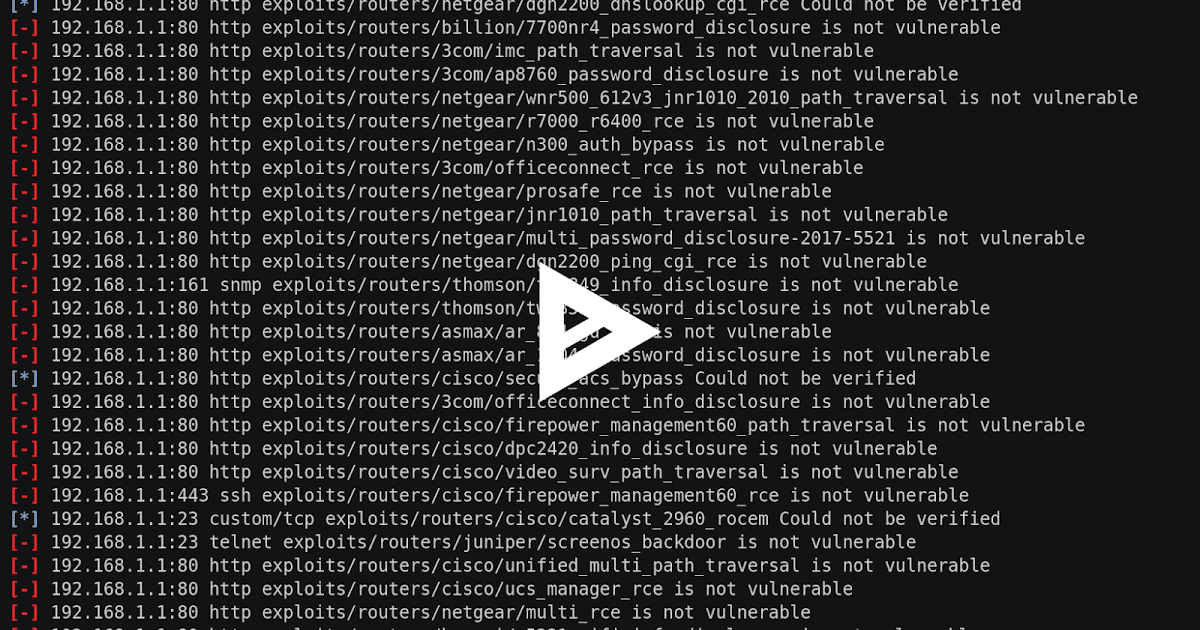
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
Search Results For - Crypto
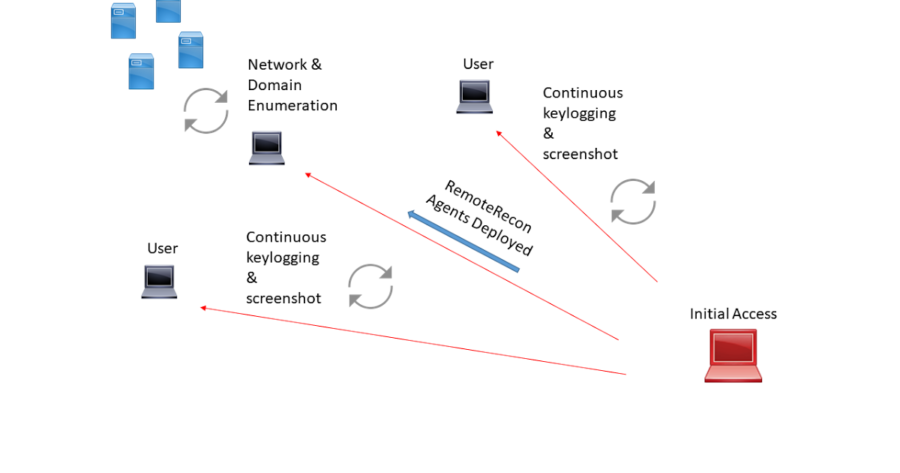
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often...
What is Cindicator? Cindicator fuses together machine learning and market analysis for asset management and financial analytics. The Cindicator team dubs this...
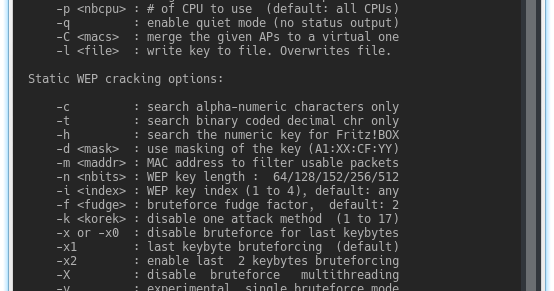
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
The aerospace industry, comprising aviation and space flight, generates trillions of dollars every year. Countries compete for the latest and greatest...
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
Airbash is a POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. It is compatible with Bash and Android Shell...
Author: Marshall Taylor Blockchains and their cryptocurrencies are energetically following a path similar to other major leaps in technology that have come...
Author: David Hamilton The banking system is inefficient in its current state as it requires the use of multiple third-party verifications and transferring...
Interview: Aragon’s Luis Cuende on Blockchain Governance & Digital Jurisdictions Author: Bennett Garner Bennett Garner: You’ve said “humans enforce...