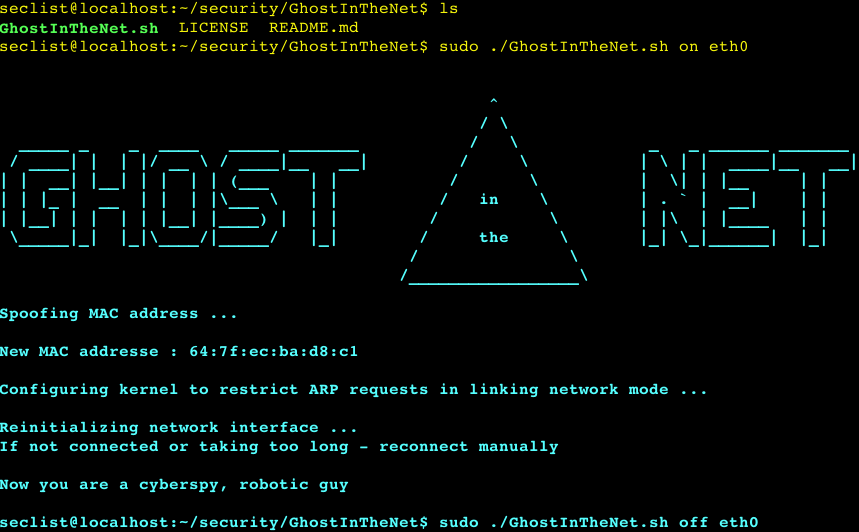
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
Search Results For - Crypto
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
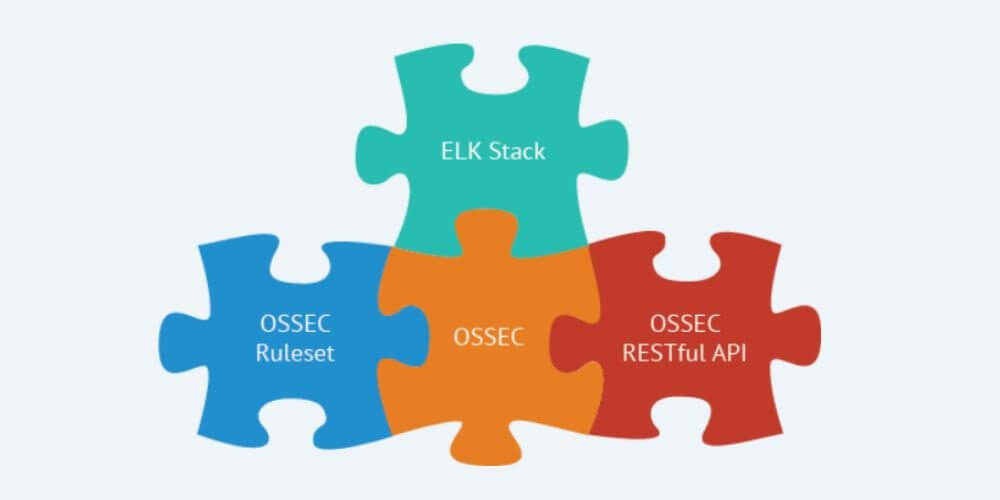
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
Bitcoin is breaking every record—after gaining 20% jump last week, Bitcoin price just crossed the $14,800 mark in less than 24 hours—and there can be no better...
The cryptocurrency fell as greatly as 8 percent on Thursday on the Luxembourg confirmed Bitstamp exchange to hit $9,000 exactly, considering a fall of well...
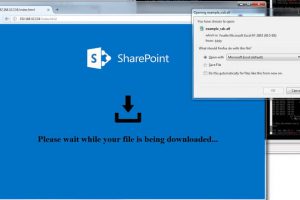
What this tool does is taking a file (any type of file), encrypt it, and embed it into an HTML file as ressource, along with an automatic download routine...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
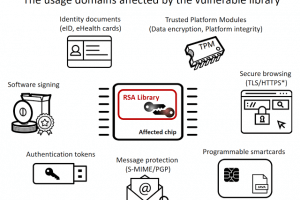
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
Bitcoin surged on Monday, recovering more than $1,000 after losing almost a third of its value in less than four days as traders bought back into the volatile...
Blockchain.info is a bitcoin cryptocurrency wallet and block explorer service. Started in August 2011, the service presents information on new transactions...