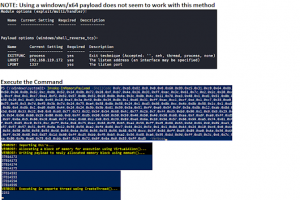
[sc name=”ad_1″] Paradoxia Remote Access Tool. Features Paradoxia Console Feature Description Easy to use Paradoxia is extremely easy to use, So...
Search Results For - C2 Server
[sc name=”ad_1″] Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1...
[sc name=”ad_1″] Widevine is a Google-owned DRM system that’s in use by many popular streaming services (Netflix, Spotify, etc.) to prevent...
[sc name=”ad_1″] What’s AutoGadgetFS ? AutoGadgetFS is an open source framework that allows users to assess USB devices and their associated...
[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
[sc name=”ad_1″] RmiTaste allows security professionals to detect, enumerate, interact and attack RMI services by calling remote methods with...
[sc name=”ad_1″] “MEDUZA” (“медуза”) means “jellyfish” in Ukrainian What is MEDUZA? It’s a Frida...
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
[sc name=”ad_1″] As indicated by sources like vulndb & cve, on a daily basis, approximately 50 new vulnerabilities become known to industry and...