[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
Search Results For - C2 Server
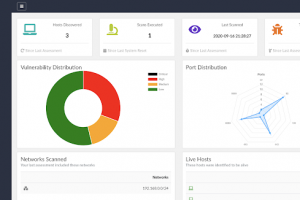
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
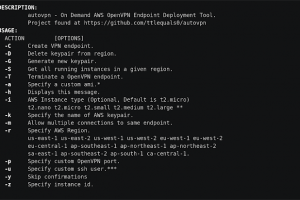
[sc name=”ad_1″] Script that allows the easy creation of OpenVPN endpoints in any AWS region. To create a VPN endpoint is done with a single...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
[sc name=”ad_1″] cnitch (snitch or container snitch) is a simple framework and command line tool for monitoring Docker containers to identify any...
[sc name=”ad_1″] Mística is a tool that allows to embed data into application layer protocol fields, with the goal of establishing a bi-directional...