[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
Tag - MITM
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] Swiss Army Knife Proxy for rapid deployments. Supports multiple operations such as request/response dump, filtering and...
[sc name=”ad_1″] Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp...
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
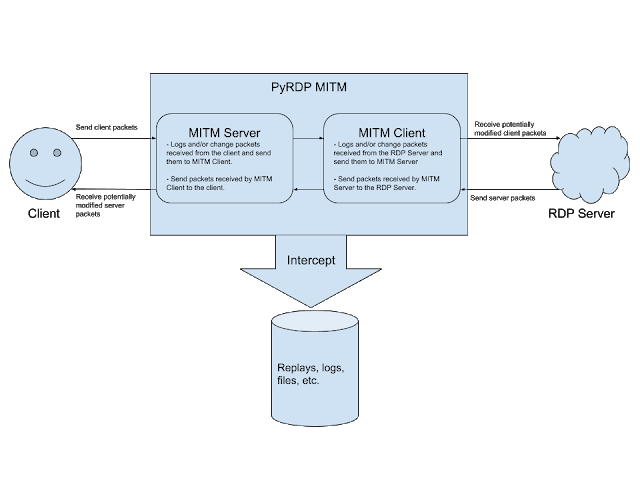
[sc name=”ad_1″] PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library. It features a few tools: RDP Man-in-the...
[sc name=”ad_1″] by Gabriel Ryan (s0lst1c3)(gryan[at]specterops.io) EAPHammer is a toolkit for performing targeted evil twin attacks against WPA2...
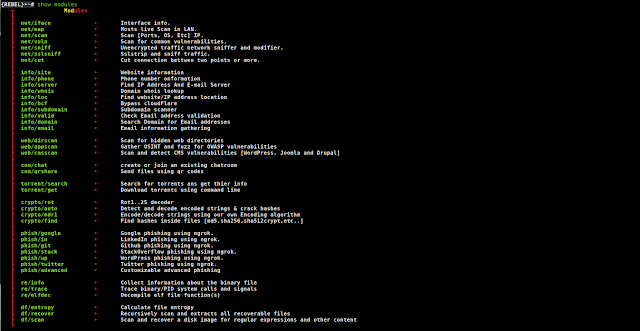
[sc name=”ad_1″] Rebel framework is an advanced and easy to use penetration testing framework.You can use it to automate the automation itself...
[sc name=”ad_1″] SKA allows you to implement a very simple and fast karma attack. You can sniff probe requests to choice the fake AP name or, if...
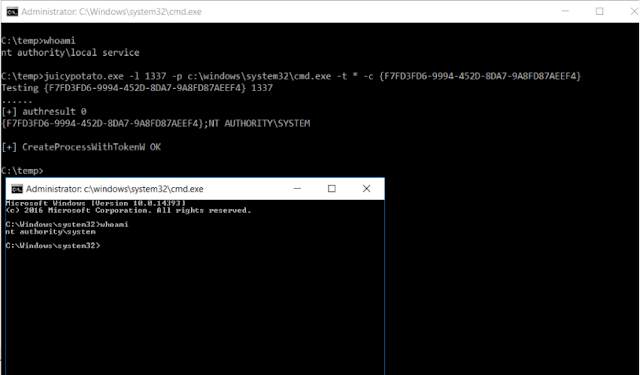
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service...