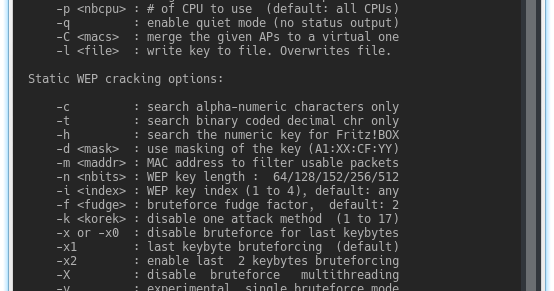
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
Search Results For - Taken
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
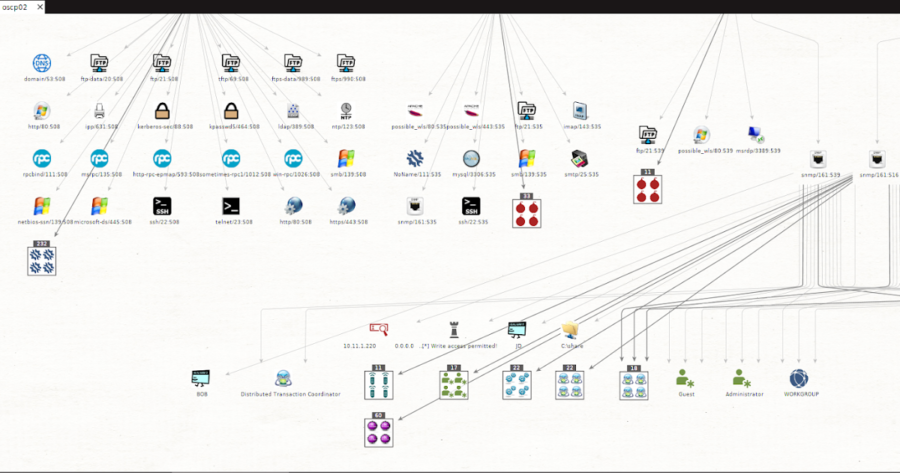
msploitego leverages the data gathered in a Metasploit database by enumerating and creating specific entities for services. Services like samba, smtp, snmp...
Author: Marshall Taylor Blockchains and their cryptocurrencies are energetically following a path similar to other major leaps in technology that have come...
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
State-of-the-art password guessing tools, such as HashCat and John the Ripper (JTR), enable users to check billions of passwords per second against password...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
In today’s world, no company is fully safe as even big names like Sony and HBO have been hacked, and quite recently Nintendo’s Switch had to go through the...