Use open source tools and network intelligence to help organizations with attack surface discovery and identification of security vulnerabilities...
Search Results For - Reverse
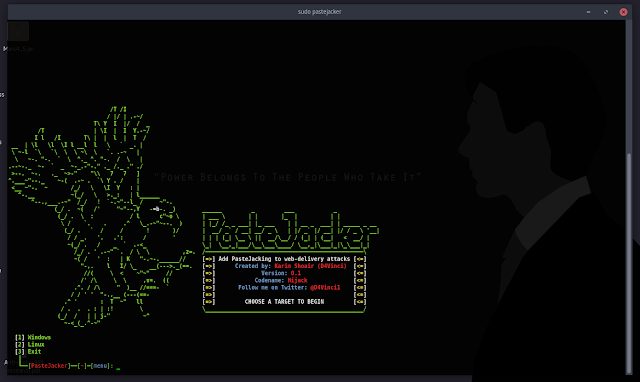
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...
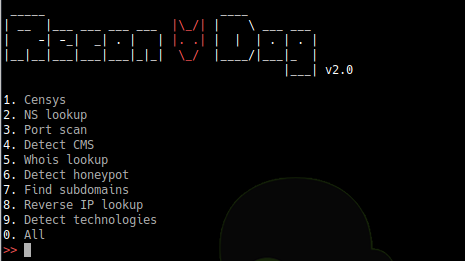
Reconnaissance Swiss Army Knife Main Features Wizard + CLA interface Can extracts targets from STDIN (piped input) and act upon them All the information is...
Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...
A Penetration Testing Framework created for Hackers / Pentester / Bug Hunter Menu Web Pentest | Banner Grab | Whois | Traceroute | DNS Record | Reverse DNS...
You can use this Framework on your website to check the security of your website by finding the vulnerability in your website or you can use this tool to Get...
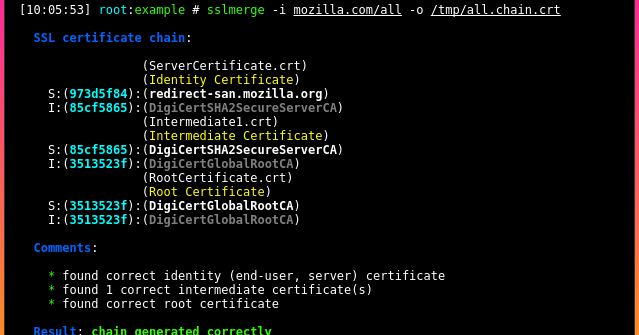
Is an open source tool to help you build a valid SSL certificate chain from the root certificate to the end-user certificate. Also can help you fix the...
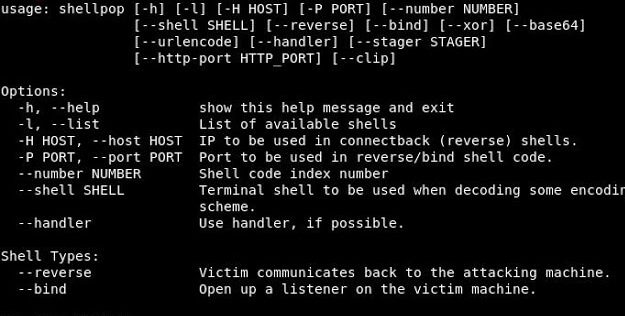
Pop shells like a master Shell pop is all about popping shells. With this tool you can generate easy and sofisticated reverse or bind shell commands to help...
[sc name=”ad_1″] Hey Guys, In this video i show you how to Embed a Metasploit Payload in an Original .Apk File. Normally we have to install the...
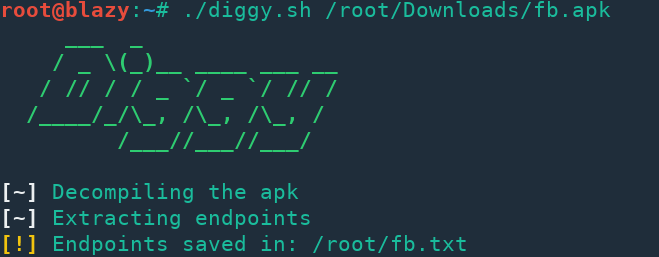
Diggy can extract endpoints/URLs from apk files. It saves the result into a txt file for further processing. Dependencies apktool Usage ./diggy.sh...