The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this attack in one place and one automated job as after searching I found there’s no tool doing this job the right way.
Now while this attack depends on what the user will paste, imagine adding this attack to Metasploit web delivery module.
See this simple scenario to make things clear:
- The target opens an HTML page served by the tool and this page has anything that makes the wants to copy from it to the terminal like some installation instructions.
- Target copies a thing from the page then it replaced quickly with our line.
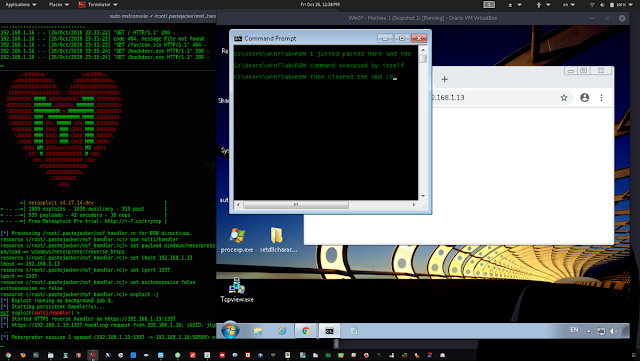
- The user pastes it in the terminal and before he notices that the line changed, the line gets executed by itself in the background and the terminal gets cleared.
- All of that happened in a second and the user sees the terminal is usable again and maybe thinks this is a bad program and he won’t install it but you already got your meterpreter shell.
This tool uses 3 methods to trick user into copying our payload instead of the command he copies:
- Using javascript to hook the copy event and replace copied data.
- Advantages :
- Anything the user copies in the page will be replaced with our line.
- Command executed by itself once target paste it without pressing enter.
- Disadvantages :
- Requires Javascript to be enabled on the target browser.
- Advantages :
- Using span style attribute to hide our lines by overwriting.
- Advantages :
- Doesn’t require javascript to be enabled.
- Works on all browsers.
- Disadvantages :
- Target must select all the text in the page or the first two words to ensure that he copies our hidden malicious lines.
- Advantages :
- Using span style again but this time to make our text transparent and non-markable.
- Advantages :
- Doesn’t require javascript to be enabled.
- Disadvantages :
- Target must select all the text in the page to ensure that he copies our hidden malicious lines.
- Not working on opera and chrome.
- Advantages :
What’s the payload user copies ?
PasteJacker gives you the option to do one of this things:
- Generate a msfvenom backdoor on our machine and the liner target gonna copy will download the backdoor on the its machine, through wget or certutil depends on the OS, then executes it on the background without printing anything to the terminal.
- Serve a liner that gets you a reverse netcat connection on the target machine running in the background of course.
- Serve your custom liner like Metasploit web-delivery payload with adding some touches to hide any possible output.
Screenshots
Installing and requirements
- Python 3 and setuptools module.
- Linux or Unix-based system (Currently tested only on Kali Linux rolling and Ubuntu 16.04).
- Third-party requirements like msfvenom but only if you are gonna use the msfvenom option of course.
- Third-party library ncurses-dev for Ubuntu (Thanks for @mhaskar).
- Root access.
Installing
- For Linux :
git clone https://github.com/D4Vinci/PasteJacker.git
sudo python3 -m pip install ./PasteJacker
sudo pastejackerUpdating the framework or the database
- On Linux while outside the directory
cd PasteJacker && git pull && cd ..
sudo python3 -m pip install ./PasteJacker --upgradeReferences
- PasteJacking GitHub repo
- Clipboard poisoning attacks on the Mac – Malwarebytes
- Metasploit web delivery module
Contact
Disclaimer
PasteJacker is created to help in penetration testing and it’s not responsible for any misuse or illegal purposes.
Copying a code from this tool or using it in another tool is accepted as you mention where you get it from.
Pull requests are always welcomed 😀






















Add Comment