CHAOS allow generate payloads and control remote Windows systems. Features Reverse Shell Download File Upload File Screenshot ? Keylogger ? Persistence Open...
Search Results For - Reverse
Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber’s powershell attacks...
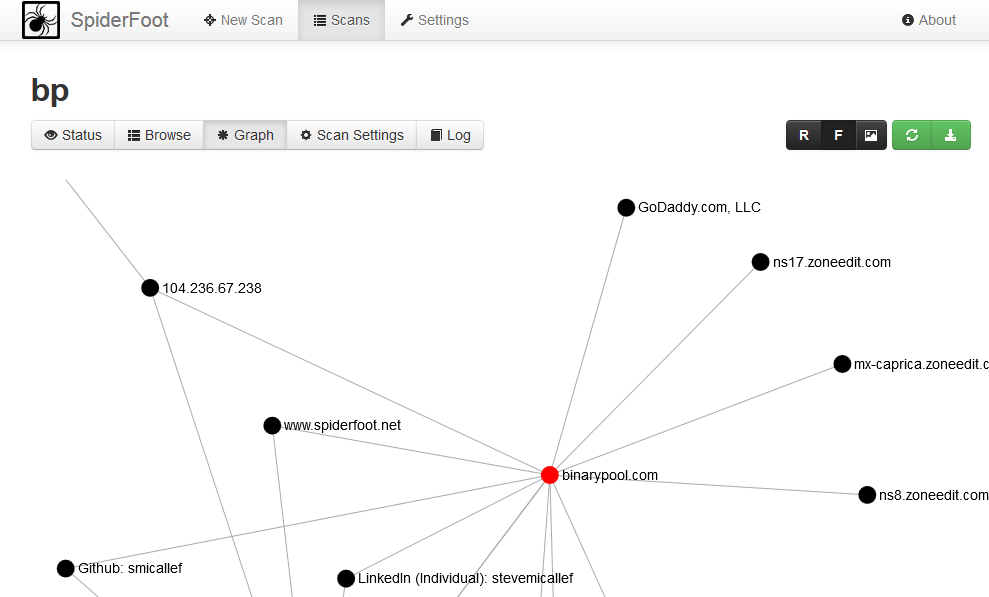
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e...
theHarvester is a tool for gathering e-mail accounts, subdomain names, virtual hosts, open ports/ banners, and employee names from different public sources...
mitmproxy is your swiss-army knife for debugging, testing, privacy measurements, and penetration testing. It can be used to intercept, inspect, modify and...
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT:...
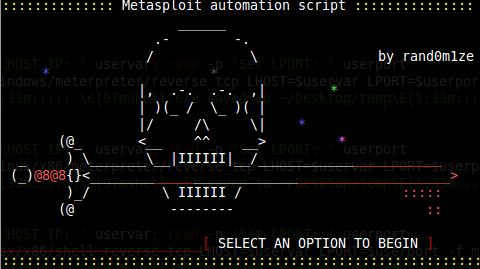
Command line script for automating metasploit functions: Checks for metasploit service and starts if not present Easily craft meterpreter reverse_tcp...
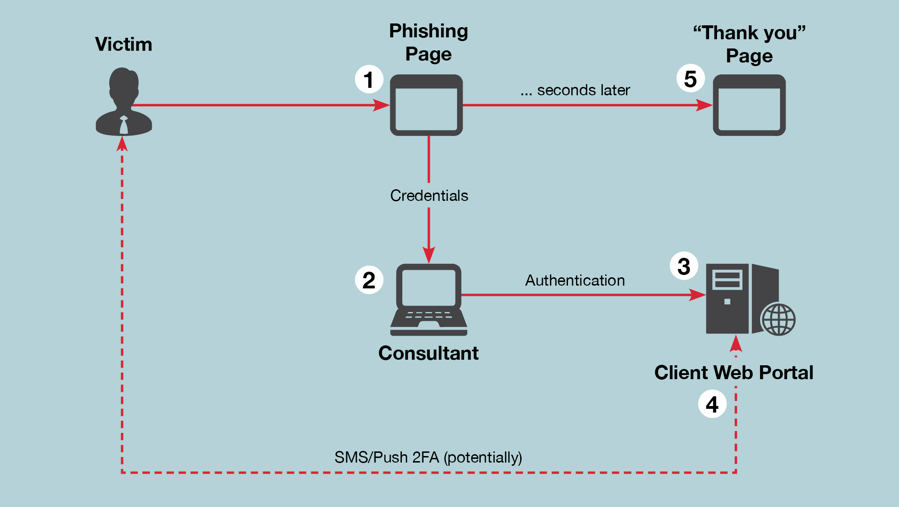
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
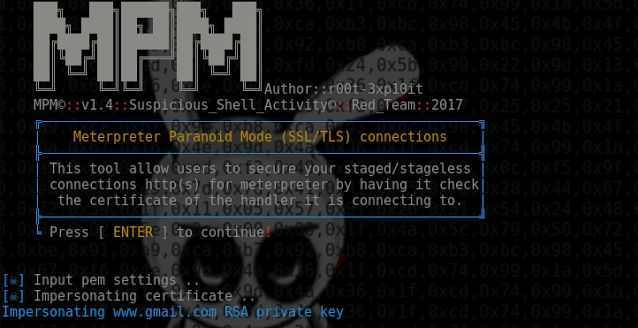
Meterpreter_Paranoid_Mode.sh allows users to secure your staged/stageless connection for Meterpreter by having it check the certificate of the handler it is...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...