[sc name=”ad_1″] A typical search engine dork scanner that scrapes search engines with queries that you provide in order to find vulnerable URLs...
Search Results For - Processes
[sc name=”ad_1″] kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in the CIS...
[sc name=”ad_1″] There are many scenarios where you would want to recover deleted data from your Mac. These deleted files could be your important...
Introduction Docker is an application that simplifies the process of managing application processes in containers. Containers let you run your applications in...
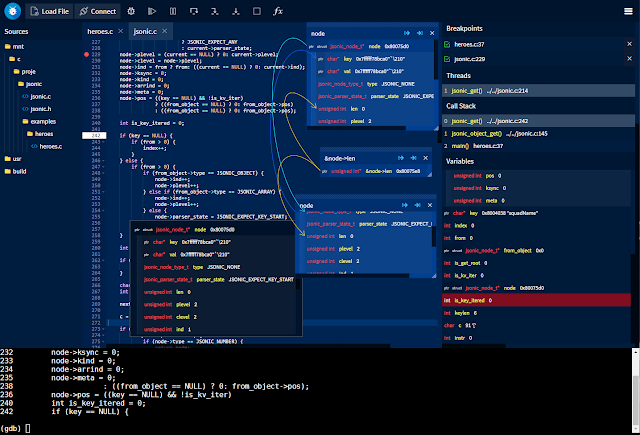
[sc name=”ad_1″] GDBFrontend is an easy, flexible and extensionable gui debugger. Installing Deb Package (Debian / Ubuntu / KDE Neon) You can...
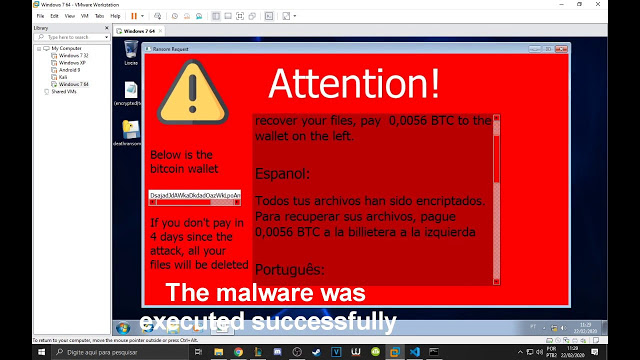
[sc name=”ad_1″] What is a ransomware? A ransomware is malware that encrypts all your files and shows a ransom request, which tells you to pay a...
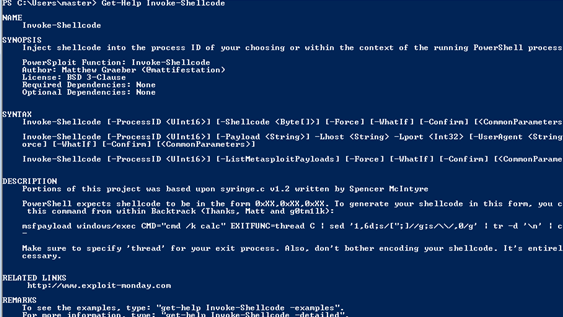
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
[sc name=”ad_1″] Semi-Automated Cyber Threat Intelligence (ACT) is a research project led by mnemonic as with contributions from the University of...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
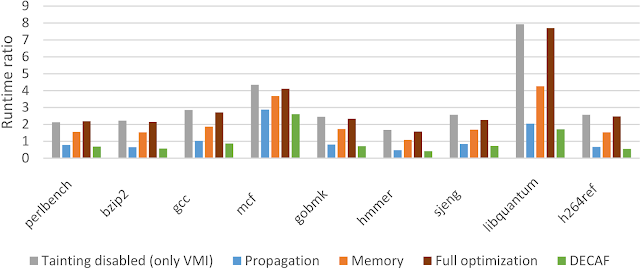
[sc name=”ad_1″] DECAF++, the new version of DECAF, taint analysis is around 2X faster making it the fastest, to the best of our knowledge, whole...