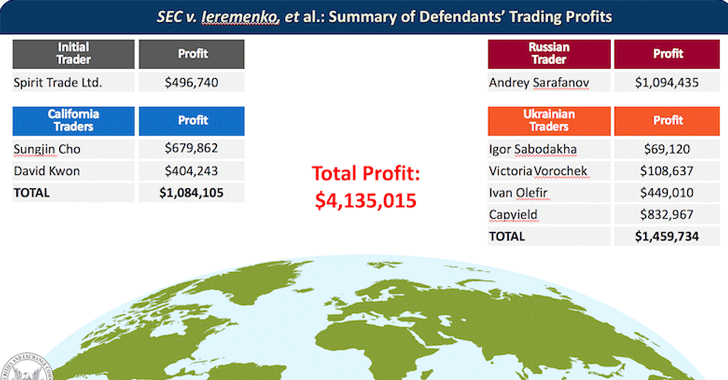
[sc name=”ad_1″] The U.S. authorities have charged two Ukrainian hackers for hacking into the Securities and Exchange Commission’s EDGAR...
Search Results For - Processes
[sc name=”ad_1″] If you are responsible for the cybersecurity of a medium-sized company, you may assume your organization is too small to be...
[sc name=”ad_1″] Another day, another data breach. This time it’s the United States National Aeronautics and Space Administration (NASA) NASA...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...
[sc name=”ad_1″] Developers of phpMyAdmin, one of the most popular and widely used MySQL database management systems, today released an updated...
[sc name=”ad_1″] Hold tight, this may blow your mind… A low-privileged user account on most Linux operating systems with UID value anything greater...
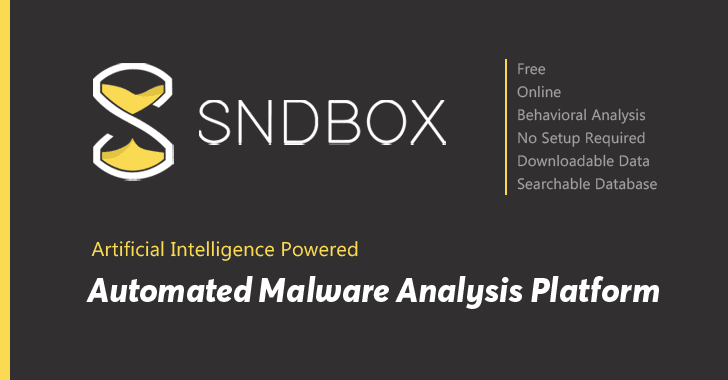
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
DEVELOPMENT BRANCH: The current branch is a development version. Go to the stable release by clicking on the master branch. Dirhunt is a web crawler optimize...
Hide your powershell script in plain sight! Invisi-Shell bypasses all of Powershell security features (ScriptBlock logging, Module logging, Transcription...
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...