[sc name=”ad_1″] A Cross Platform Remote Administration tool written in Go using Tor as its transport mechanism currently supporting Windows...
Search Results For - Procedure
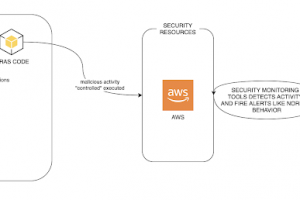
[sc name=”ad_1″] Security Incident Response Automated Simulations (SIRAS) are internal/controlled actions that provide a structured opportunity to...
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
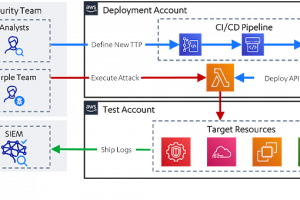
[sc name=”ad_1″] Leonidas is a framework for executing attacker actions in the cloud. It provides a YAML-based format for defining cloud attacker...
[sc name=”ad_1″] Cloud Security Operations What is Cloud Sniper? Cloud Sniper is a platform designed to manage Security Operations in cloud...
[sc name=”ad_1″] SkyArk is a cloud security project with two main scanning modules: AzureStealth – Scans Azure environments AWStealth –...
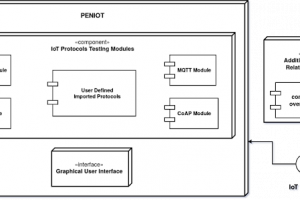
[sc name=”ad_1″] PENIOT is a penetration testing tool for Internet of Things (IoT) devices. It helps you to test/penetrate your devices by...
[sc name=”ad_1″] Mail transfer is a common search query. Most commonly, users may migrate due to personal preferences, corporate policies, or...
[sc name=”ad_1″] Spam is a common nuisance for users of the Internet. However, it is not just annoying – these messages may cause substantial...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...