A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
Search Results For - Procedure
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT:...
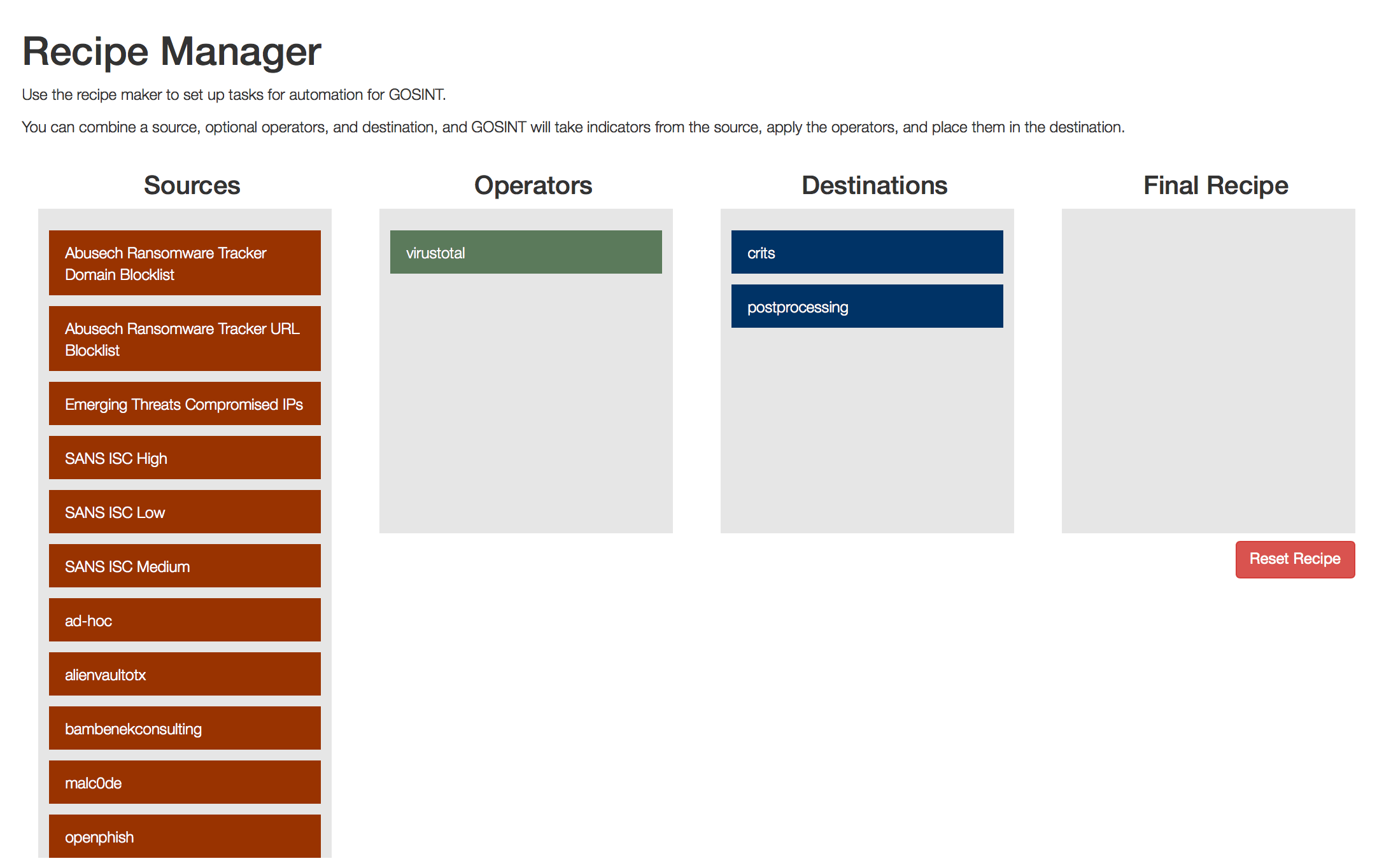
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Security researchers from FireEye and Dragos have discovered a nasty piece of malware targeting industrial control systems (ICS). The malware (called “TRITON”...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
Now security researchers have discovered that the camera can be silenced and frozen from a script run from any machine within Wi-Fi range, reports News. That...
Unfortunately, it looks like the method is still in effect. Philip Neustrom, the co-founder of Shotwell Labs, lately found two demo websites that would pass...
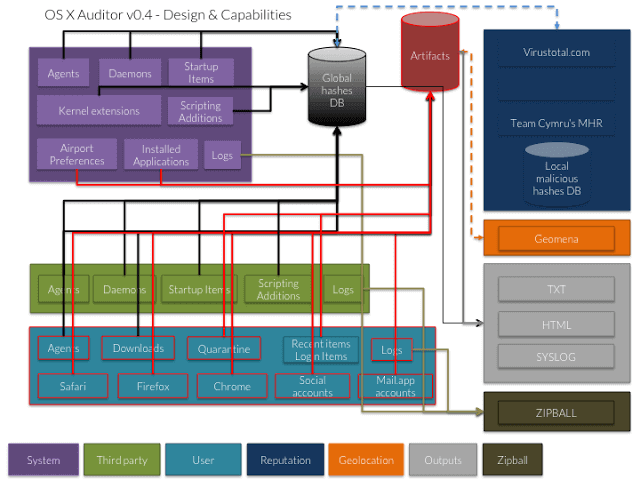
OS X Auditor is a free Mac OS X computer forensics tool. OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you...
Do you know—United States Government has banned federal agencies from using Kaspersky antivirus software over spying fear? Though there’s no solid...