The prosecutions were filed in California, Oregon, and Indiana, according to The News. The three incidents focus on the setback in Intel disclosing the...
Search Results For - Mac OS X
One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...
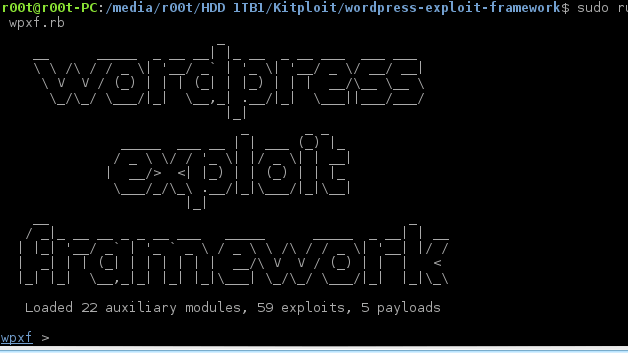
A Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems. What do I need to run it...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
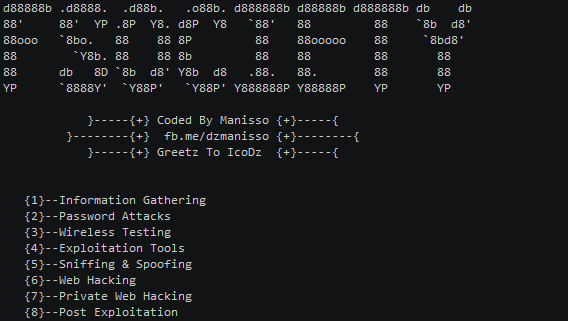
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
NTU researchers have revealed that smartphones can now be hacked using the data accumulated from sensors. Dr. Shivam, a scientist at NTU, who recently...
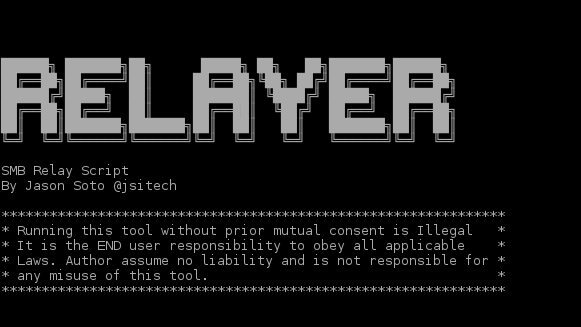
Relayer is an SMB relay Attack Script that automates all the necessary steps to scan for systems with SMB signing disabled and relaying authentication request...
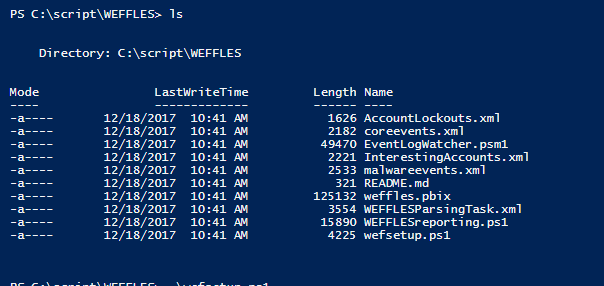
WEFFLES is designed to be small and lightweight, both for speed of getting something deployed during an Incident Response and also for the sake of being...
BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...