mitm6 is a pentesting tool that exploits the default configuration of Windows to take over the default DNS server. It does this by replying to DHCPv6 messages...
Search Results For - Hardware
SDRtrunk is an integrated application for demodulating radio signals and decoding trunked radio network protocols and some related radio signal formats. The...
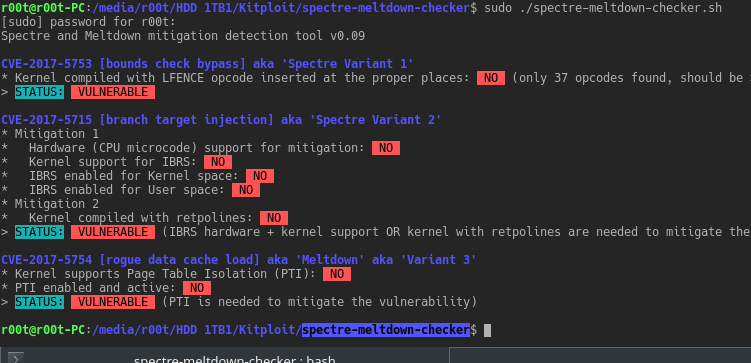
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
In today’s world, no company is fully safe as even big names like Sony and HBO have been hacked, and quite recently Nintendo’s Switch had to go through the...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
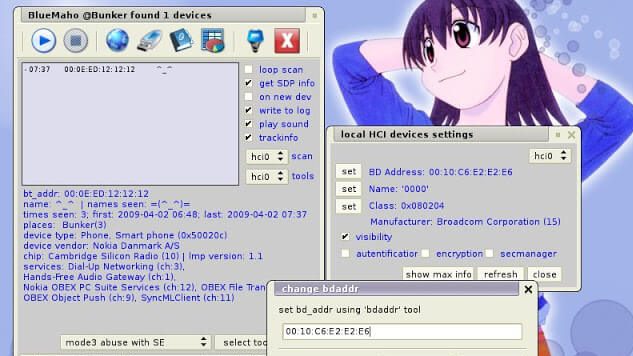
BlueMaho is GUI-shell (interface) for suite of tools for testing security of bluetooth devices. It is freeware, opensource, written on python, uses wxPyhon. It...
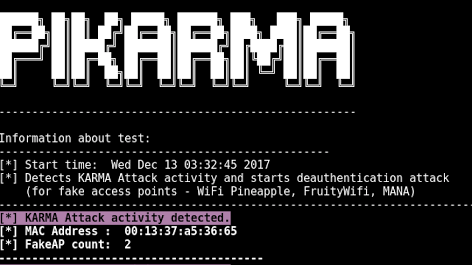
Detects wireless network attacks performed by KARMA module (fake AP). Starts deauthentication attack (for fake access points) Working Principle for PiKarma...
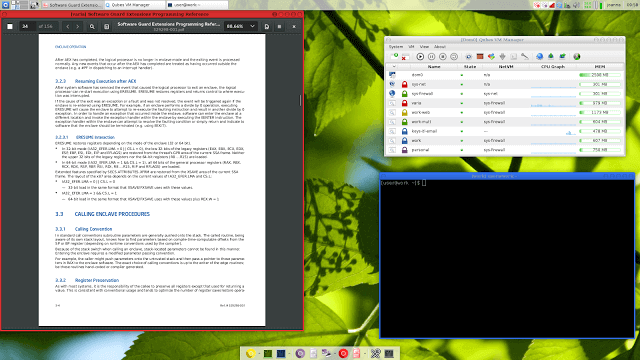
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...