Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...
Search Results For - Hardware
Device drivers are an essential part in modern Unix-like systems to handle operations on physical devices, from hard disks and printers to digital cameras and...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
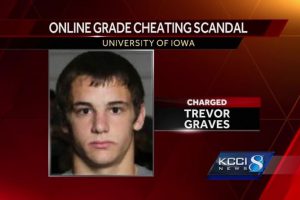
The FBI apprehended the suspect Trevor Graves, age 22 at the close of October, in Denver, his hometown. According to an FBI arrest warrant, the teen planted...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing...
News reported the issue, revealing a picture of a Pixel 2 XL with some fierce image remembrance around the navigation bar. Shortly after, numerous other...
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
Joe Belfiore continued that he had also shifted to Android himself. Windows 10 Mobile attempted to attract users by making them run the same “universal apps”...