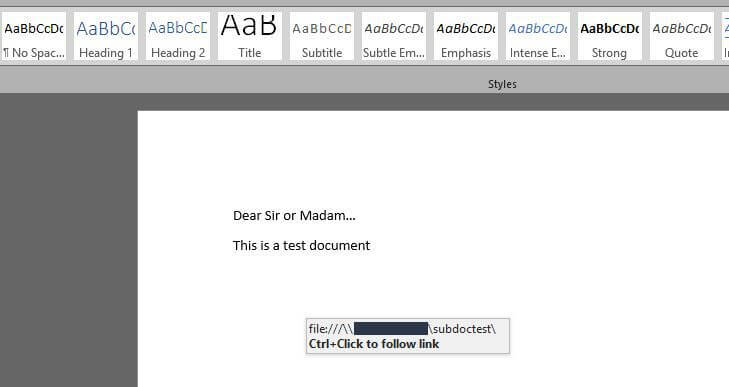
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
Search Results For - Cyber
shimit is a python tool that implements the Golden SAML attack. python .\shimit.py -h usage: shimit.py [-h] -pk KEY [-c CERT] [-sp SP] -idp IDP -u USER [-reg...
The prosecutions were filed in California, Oregon, and Indiana, according to The News. The three incidents focus on the setback in Intel disclosing the...
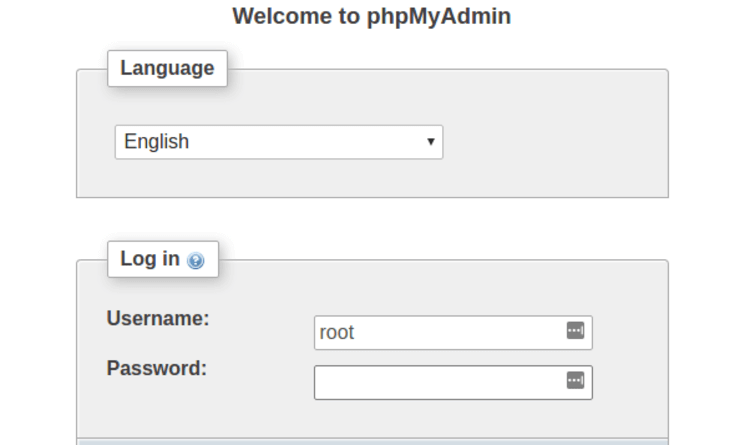
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...
A breach of Forever 21 left consumer payment card data exposed to hackers, the retailer verified Thursday. The business didn’t specify how many customers had...
Quite recently, the founder of Mcafee company, John Mcafee, was in news when his Twitter was hacked by an unknown hacker. This hacker used John’s social media...
Zachary Buchta, a 20 year old hacker, who is the co-founder of famous hacking groups called Lizard Squad And Poodlecorp was recently in news for all the wrong...
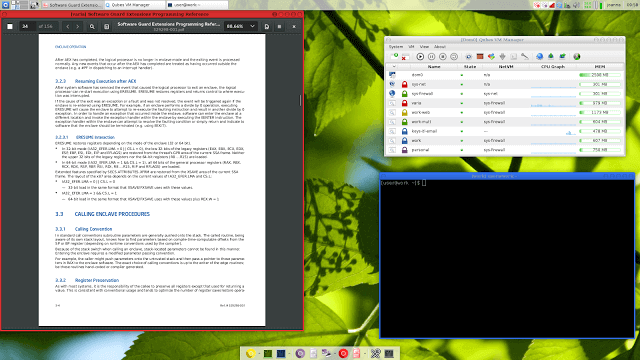
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
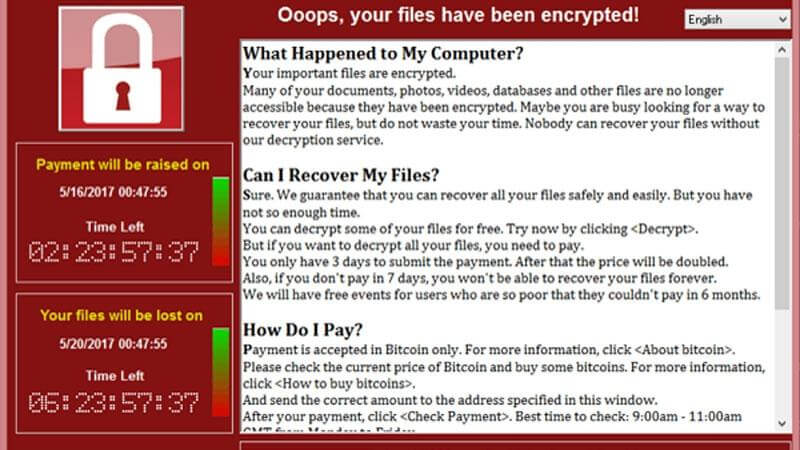
North Korea says there is no evidence to back the US claim it was behind the WannaCry ransomware attack. The US was “unreasonably accusing the DPRK...