Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...
Search Results For - Command Line
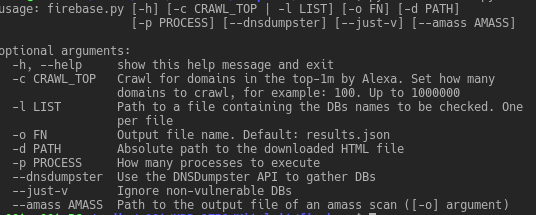
Exploiting vulnerable/misconfigured Firebase databases Prerequisites Non-standard python modules: dnsdumpster bs4 requests Installation If the following...
The aerospace industry, comprising aviation and space flight, generates trillions of dollars every year. Countries compete for the latest and greatest...
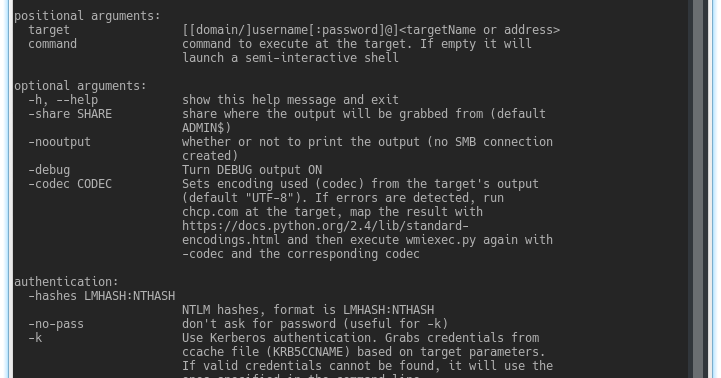
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
Hey Guys, In this video i show you how to perform Wi-Fi deauthentication attack on any Wi-Fi Network. Wi-Fi deauthentication attack is a type of denial-of...
This is Part 2 of Linux Basics In this Part we will talk about your first steps with linux. Logging In and Out: The Linux system distinguishes between...
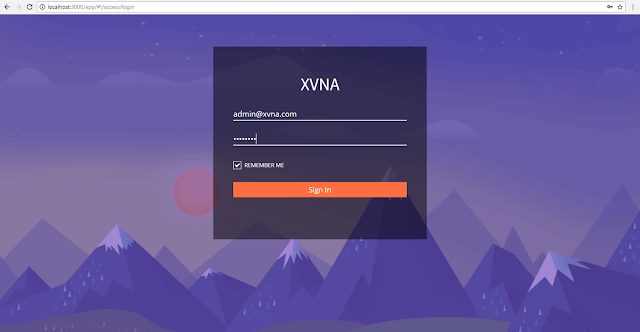
XVNA is an extreme vulnerable node application coded in Nodejs(Expressjs)/MongoDB that helps security enthusiasts to learn application security. it’s not...
Hardentools is a collection of simple utilities designed to disable a number of “features” exposed by operating systems (Microsoft Windows, for now), and...
mitmproxy is your swiss-army knife for debugging, testing, privacy measurements, and penetration testing. It can be used to intercept, inspect, modify and...