[sc name=”ad_1″]
It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable websites that have not yet applied patches already available by its developers, but hackers are also exploiting a critical WinRAR vulnerability that was also revealed last week.
A few days ago, The Hacker News reported about a 19-year-old remote code execution vulnerability disclosed by Check Point in the UNACEV2.dll library of WinRAR that could allow a maliciously-crafted ACE archive file to execute arbitrary code on a targeted system.
WinRAR is a popular Windows file compression application with 500 million users worldwide, but a critical “Absolute Path Traversal” bug (CVE-2018-20250) in its old third-party library, called UNACEV2.DLL, could allow attackers to extract a compressed executable file from the ACE archive to one of the Windows Startup folders, where the file would automatically run on the next reboot.
To successfully exploit the vulnerability and take full control over the targeted computers, all an attacker needs to do is just convincing users into opening a maliciously-crafted compressed archive file using WinRAR.
Just a day after the Check Point’s blog post and a proof of concept video (that showcased how an ACE archive can extract a malicious file into the Windows Startup folder) went public, a Proof-of-concept (PoC) exploit code for the newly discovered WinRAR vulnerability was published to Github.
What’s worse?
Security researchers at the 360 Threat Intelligence Center (360TIC) just yesterday detected an in-the-wild malspam email campaign that’s distributing a malicious RAR archive file that exploits the latest WinRAR vulnerability to install malware on computers running the vulnerable version of the software.
“Possibly the first malware delivered through the mail to exploit WinRAR vulnerability. The backdoor is generated by MSF [Microsoft Solutions Framework] and written to the global startup folder by WinRAR if UAC is turned off,” the researchers tweeted.
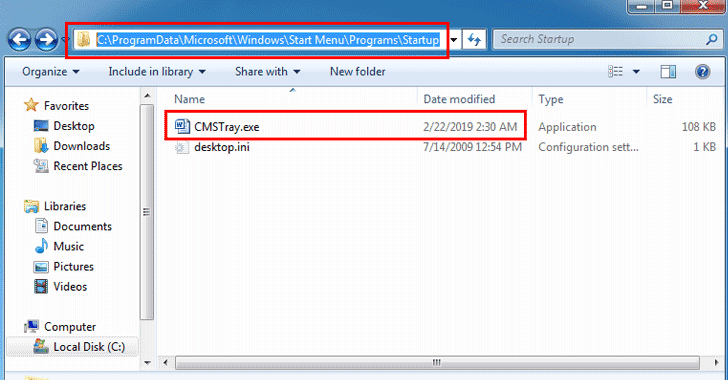
As shown in the screenshot shared by the researchers, when opened using WinRAR—software running with administrator privileges or on a targeted system with UAC (User Account Control) disabled—the malware drops a malicious exe file (CMSTray.exe) to the Windows Startup folder, designed to infect the targeted computer with a backdoor.
Since UAC puts some limitations on permissions, attempting to extract the archive with UAC enabled fails to place the malicious exe file in the C:ProgramData folder, thus failing to infect the computer.
The best way to protect yourself from these attacks is to update your software by installing the latest version of WinRAR as soon as possible and avoid opening files received from unknown sources.
Since the WinRAR team had lost the access to the source code for the vulnerable UNACEV2.DLL library in 2005, instead of fixing the issue, it released WINRar version 5.70 beta 1 that doesn’t support the DLL and ACE format. This fix addressed the bug, but at the same time also removes all ACE support from WinRAR.




















Add Comment