The Guasap Forensic implemented in Python under the GNU General Public License, for the extraction and analysis of files, data bases and logs for forensic...
Category - Information Gathering
Information gathering is the most time-consuming and laborious phase of the attack cycle but is often a major determinant of the success or failure of the engagement.
SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
You can use this Framework on your website to check the security of your website by finding the vulnerability in your website or you can use this tool to Get...
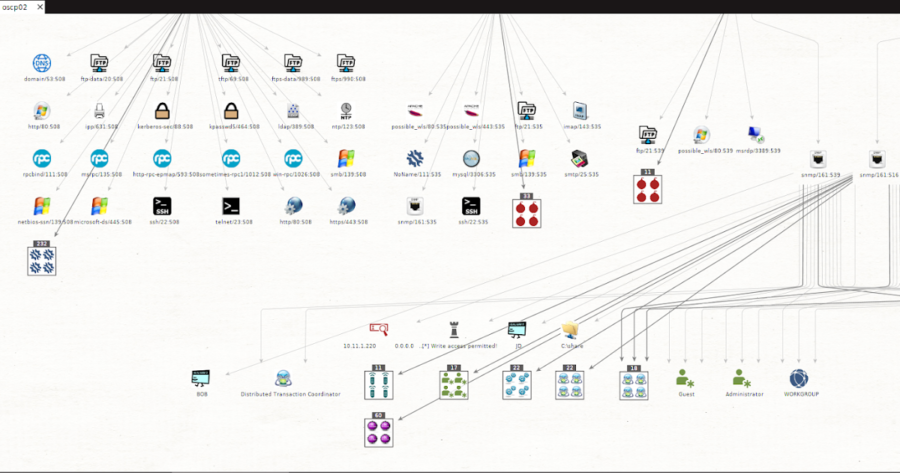
msploitego leverages the data gathered in a Metasploit database by enumerating and creating specific entities for services. Services like samba, smtp, snmp...
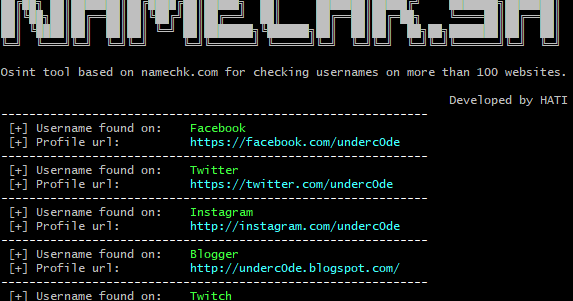
Osint tool based on namechk.com for checking usernames on more than 100 websites, forums and social networks. Use: Search available username: ./namechk.sh...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
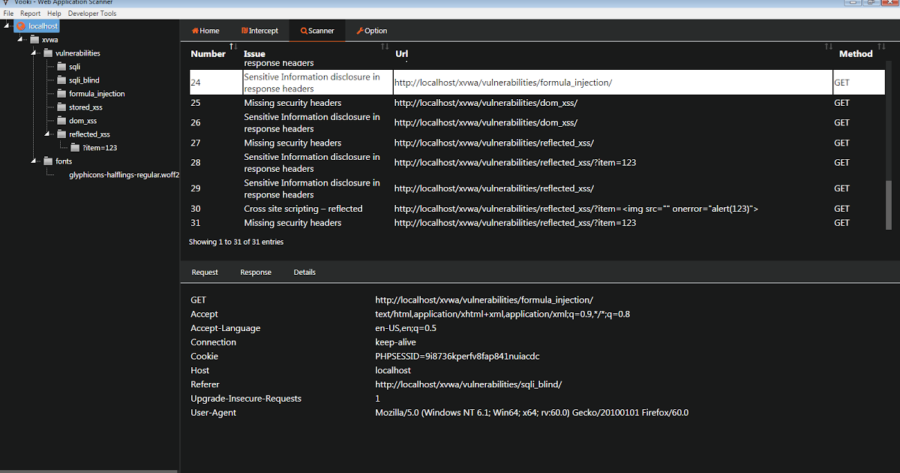
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities...
pwnedOrNot is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find...
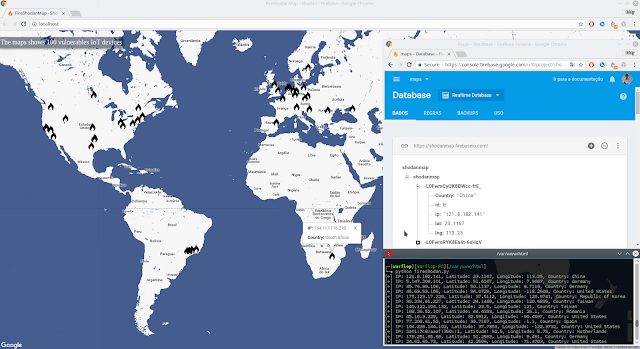
FireShodanMap is a Realtime map that integrates Firebase and Shodan. A search is carried out using Shodan searching vulnerable devices and they are showed on...
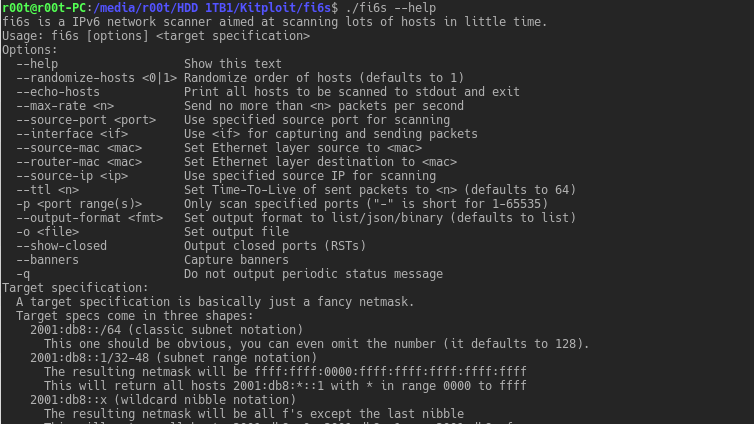
fi6s is a IPv6 port scanner designed to be fast. This is achieved by sending and processing raw packets asynchronously. The design and goal is pretty similar...