[sc name=”ad_1″]
Late last year when an unknown group of hackers stole secret access tokens for millions of Facebook accounts by taking advantage of a flaw in its website, the company disclosed the incident and informed its affected users.
Similarly, when Twitter was hit by multiple vulnerabilities (#1, #2, #3) in the last few months, the social media company disclosed those incidents and informed its affected users.
And Guess What? Google is going to shut down its social media network Google+ in April this year after admitting two security flaws in its platform that exposed private data of hundreds of thousands of users to third-party developers.
It turns out that Apple also possibly suffered a privacy breach late last year due to a bug in its platform that might have exposed some of your iCloud data to other users, but the company chose to keep the incident secret… maybe because it was not worth to disclose, or perhaps much more complicated.
Last week, Turkish security researcher Melih Sevim contacted The Hacker News and claimed to have discovered a flaw in Apple services that allowed him to view partial data, especially notes, from random iCloud accounts as well as on targeted iCloud users just by knowing their associated phone numbers.
[youtube https://www.youtube.com/watch?v=OnKVD_5e8uA]
Melih confirmed The Hacker News that he discovered the alleged flaw in October 2018, and then responsibly reported it to the Apple’s security team with steps to reproduce the bug and a video demonstration, showing how he was able to read personal iCloud data from other Apple users without their knowledge.
“I discovered that when there is an active data transfer between the user and Apple servers if I open my (attacker’s) iCloud account, there is a possibility to view some random data on every refresh due to the bug,” Melih told The Hacker News.
After patching it in November 2018, Apple acknowledged the issue to Melih but responded that the company had already addressed it before receiving details from him.
Apple then immediately closed the ticket and buried the lead.
A Mysterious iCloud Bug
Based upon Melih explanation, the alleged flaw resided in the way Apple “internally” linked, either accidentally or intentionally, a phone number saved in the billing information of an Apple ID to the iCloud account on a device using the same phone number.
According to Melih, after following some specific steps on his iPhone and then saving a new phone number linked to another Apple ID in the billing information related settings on his device, he was able to view partial iCloud data from the account associated with that number.
“Let suppose, if [email protected]’s mobile number is 12345 and when I enter 12345 mobile number to my [email protected] Apple ID account, I could see abc’s data on xyz’s account,” Melih told THN.
“During my researcher, I saw many notes from other Apple users who kept their bank account related information and passwords in the iCloud.”
Since the flaw was in the section of iCloud settings for iOS devices that load from Apple servers in real-time using the Internet, it was silently patched by Apple team from the background without releasing a new iOS update.
If Melih’s report is accurate, the next detail makes the issue more serious…
Melih also confirmed The Hacker News that the text-box asking users to enter a phone number was not validating the user input, thus allowing an attacker even to save a single digit input.
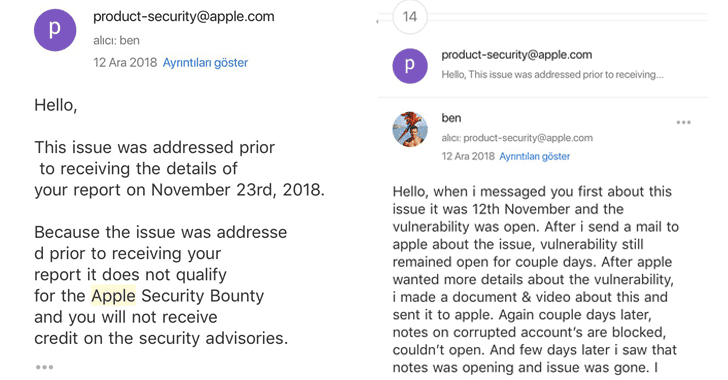
As shown in the video demonstration shared by Melih with THN, the trick eventually exploited the same flaw into fetching personal data from random iCloud accounts matching the input digit to their associated phone numbers.
Apple Acknowledged the Problem, But…
To confirm Melih’s bug and know the full extent of the incident, we reached out to the Apple security team before publishing this article.
In response to The Hacker News email and knowing that we are working on a story, Apple acknowledged the bug report, saying “the issue was corrected back in November,” without responding to some other important questions, including for how many weeks the flaw remained open, the estimated number of affected users (if any) and if there is any evidence of malicious exploitation?
Well, that was weird, but not new…
Just yesterday, Apple temporarily took down its Group FaceTime service after the public disclosure of a bug in its video-calling app that allows FaceTime users to hear or see other users before they even pick up the call.
Later it turned out that Apple was apparently notified of the FaceTime eavesdropping bug over a week ago by a 14-year-old boy before it made headlines, but again, the Apple security team failed to communicate promptly, leaving its millions of users unaware of the issue and at risk.
If the suspected iCloud leak was minor, then Apple could have confirmed us, but it’s silence over the report makes the incident more suspicious.
We’ll update this story as we hear more.





















Add Comment