Bashark aids pentesters and security researchers during the post-exploitation phase of security audits. Usage To launch Bashark on compromised host, simply...
Archive - October 2018
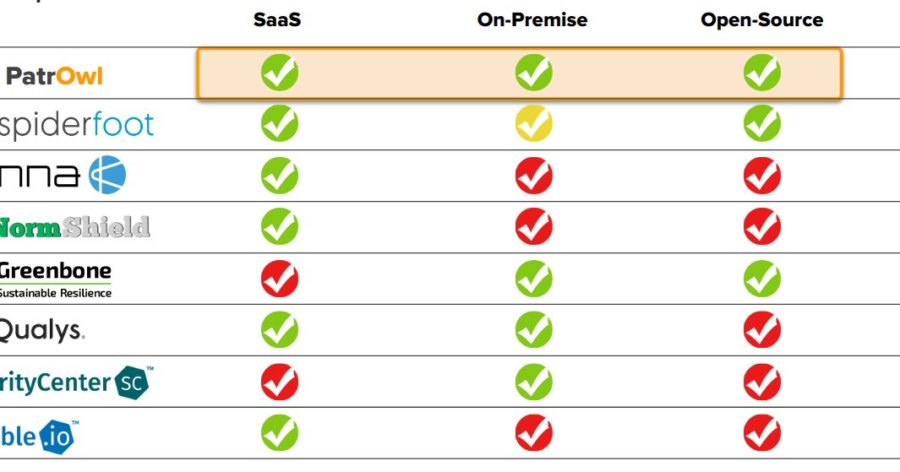
PatrOwl is a scalable, free and open-source solution for orchestrating Security Operations. PatrowlManager is the Front-end application for managing the...
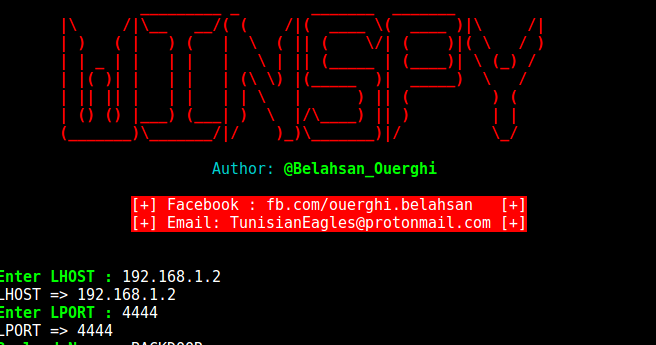
WinSpy: Windows Reverse Shell Backdoor Creator With ip poisener. Dependencies 1 – metasploit-framework 2 – xterm 3 – apache2 4 –...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...
Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
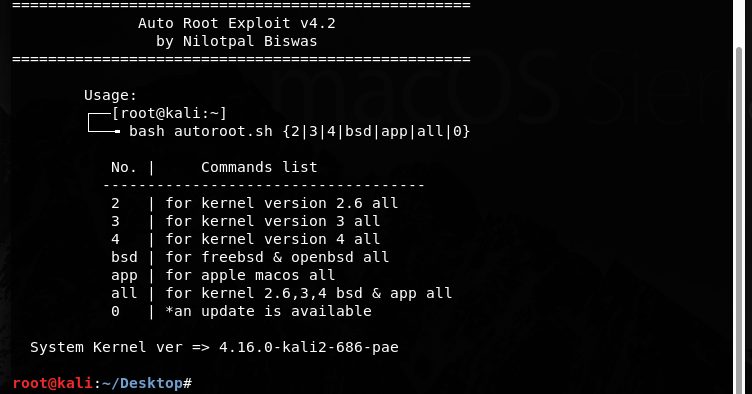
Auto Root Exploit Tool Author : Nilotpal Biswas Facebook : Twitter : USAGE : for kernel version 2.6 all bash autoroot.sh 2 for kernel version 3 all bash...
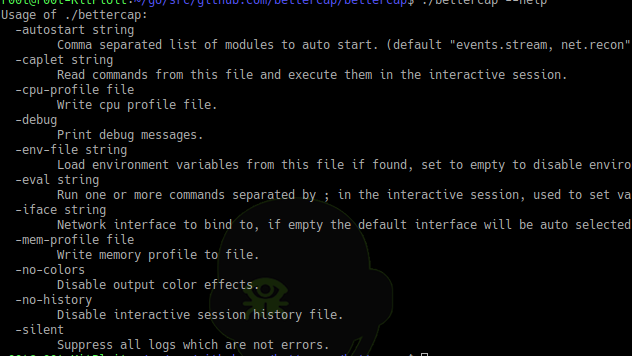
bettercap is the Swiss Army knife for 802.11, BLE and Ethernet networks reconnaissance and attacks. How to Install A precompiled version is available for each...
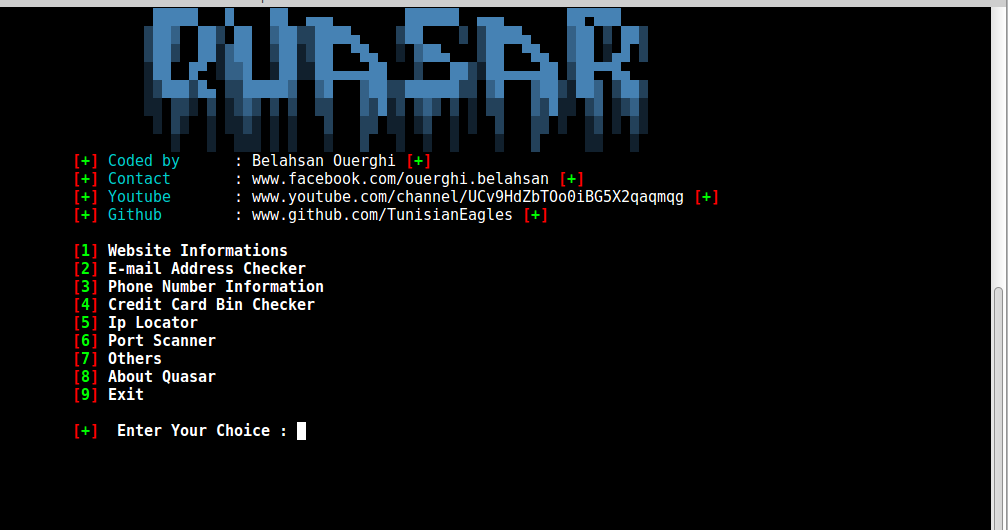
Quasar Is An Information Gathering Framework For Penetration Testers Coded By Belahsan Ouerghi: Website Informations E-mail Address Checker Phone Number...
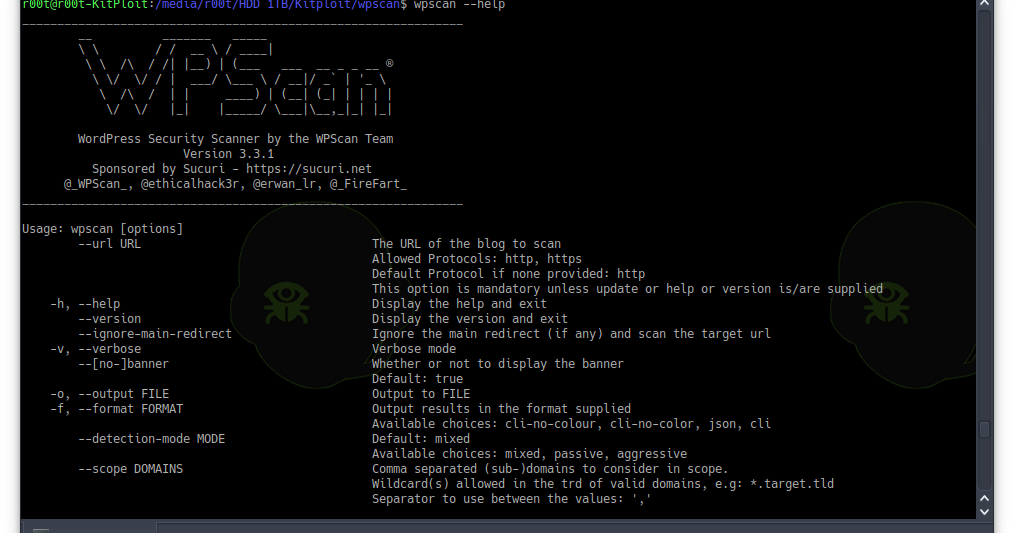
WPScan is a free, for non-commercial use, black box WordPress vulnerability scanner written for security professionals and blog maintainers to test the...