[sc name=”ad_1″]
Well, there’s some good news for hackers and vulnerability hunters, though terrible news for tech manufacturers!
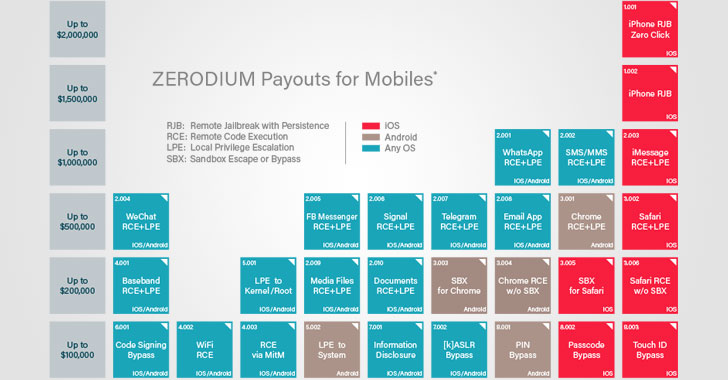
Exploit vendor Zerodium is now willing to offer significantly higher payouts for full, working zero-day exploits that allow stealing of data from WhatsApp, iMessage and other online chat applications.
Zerodium—a startup by the infamous French-based company Vupen that buys and sells zero-day exploits to government agencies around the world—said it would now pay up to $2 million for remote iOS jailbreaks and $1 million for exploits that target secure messaging apps.
Get $2 Million for Remotely Jailbreaking An iPhone
Previously, Zerodium was offering $1.5 million for persistent iOS jailbreaks that can be executed remotely without any user interaction (zero-click)—but now the company has increased that amount to $2 million.
The company is now offering $1.5 million for a remote iOS jailbreak that requires minimal user interaction (i.e., single-click)—the amount has increased from $1 million.
Get $1 Million for Selling WhatsApp and iMessage Zero-Days
Zerodium has also doubled the price for remote code execution (RCE) exploits that target secure-messaging apps like WhatsApp, iMessage, and SMS/MMS apps for all mobile operating systems, making it 1 million from $500,000.
However, the price for zero-day exploits for popular encrypted app Signal that’s widely used by many technologists, journalists, and lawyers remained at $500,000, same as before.
Other Zero-Day Buyout Offers
Here’s the list of revised prices announced Monday by Zerodium for a variety of other exploits:
- $1 million for zero-click remote code execution exploits in Windows (previously $500,000)
- $500,000 for remote code-execution exploits in Chrome including a sandbox escape (previously $250,000 and $200,000 for Windows and Android respectively)
- $500,000 for Apache or Microsoft IIS RCEs, i.e., remote exploits via HTTP(S) requests (previously $250,000)
- $500,000 for local privilege escalation attacks against Safari including a sandbox escape (previously $200,000)
- $250,000 for Outlook RCEs, i.e., remote exploits via malicious emails (previously $150,000)
- $250,000 for PHP or OpenSSL RCEs (previously $150,000)
- $250,000 for Microsoft Exchange Server RCEs (previously $150,000)
- $200,000 for Local privilege escalation to either kernel or root for Android or iOS operating system (previously $100,000)
- $200,000 for VMWare ESXi Virtual Machine Escape i.e. guest-to-host escape (previously $100,000)
- $100,000 for Local pin/passcode or Touch ID bypass for Android or iOS (previously $15,000)
- $80,000 for Windows local privilege escalation or sandbox escape (previously $50,000)
The hike in the price is in line with demand and the tougher security of the latest operating systems and messaging apps, as well as to attract more researchers, hackers and bug hunters to seek complex exploit chains.
The amount paid by Zerodium to researchers for acquiring their original zero-day exploits depends on the popularity and security level of the affected software or system, as well as the quality of the submitted exploit, like is it a full or partial chain, does it affect current versions, reliability, bypassed exploit mitigations, process continuation and so on.
To claim the prize money, your research must be original and previously unreported. Zerodium also said that the company is willing to pay even higher rewards to researchers for their exceptional exploits or research.
Hackers will get the payout within a week of submitting the zero-day exploits along with a valid working proof-of-concept.
Recently, Zerodium disclosed a critical zero-day vulnerability in the NoScript browser plugin that could have been exploited to execute malicious JavaScript on victims’ Tor browsers to effectively identify their real IP address even if the maximum security level was used.




















Add Comment