[sc name=”ad_1″]
A zero-day vulnerability has been discovered and reported in the Microsoft’s Windows operating system that, under a certain scenario, could allow a remote attacker to execute arbitrary code on Windows machine.
Discovered by security researcher John Page (@hyp3rlinx), the vulnerability was reported to the Microsoft security team through Trend Micro’s Zero Day Initiative (ZDI) Program over 6 months ago, which the tech giant has refused to patch, at least for now.
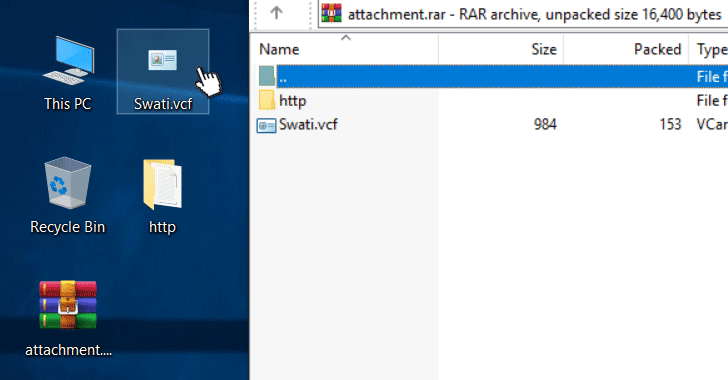
The vulnerability, which has not been assigned any CVE number, actually resides within the processing of a vCard file—a standard file format for storing contact information for a person or business, which is also supported by Microsoft Outlook.
According to the researcher, a remote attacker can maliciously craft a VCard file in a way that the contact’s website URL stored within the file points to a local executable file, which can be sent within a zipped file via an email or delivered separately via drive-by-download techniques.
As shown in the video demonstration, if a victim clicks that website URL, the Windows operating system would run the malicious executable without displaying any warning, instead of opening the web address on the browser.
“Crafted data in a VCard file can cause Windows to display a dangerous hyperlink,” the researcher writes in an advisory. “The user interface fails to provide any indication of the hazard. An attacker can leverage this vulnerability to execute code in the context of the current user.”
Obviously, “user interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.”
Although the attack requires user’s interaction, leaving the vulnerability unpatched would leave an opportunity for sophisticated attackers to target Windows users at large.
The researcher has also published proof-of-concept exploit code for the vulnerability, which has been assigned a CVSS 3.0 score of 7.8.




















Add Comment