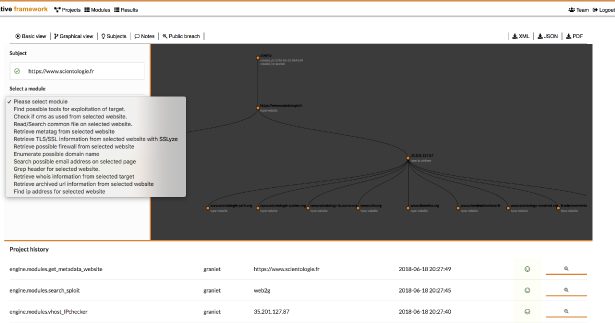
You can use this Framework on your website to check the security of your website by finding the vulnerability in your website or you can use this tool to Get...
Tag - python
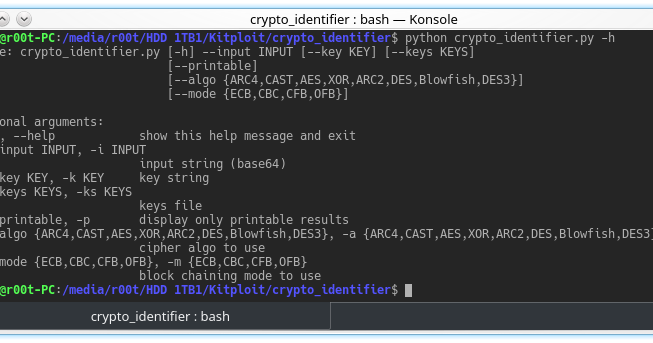
Crypto tool for pentest and ctf : try to uncipher data using multiple algorithms and block chaining modes. Usefull for a quick check on unknown cipher text and...
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
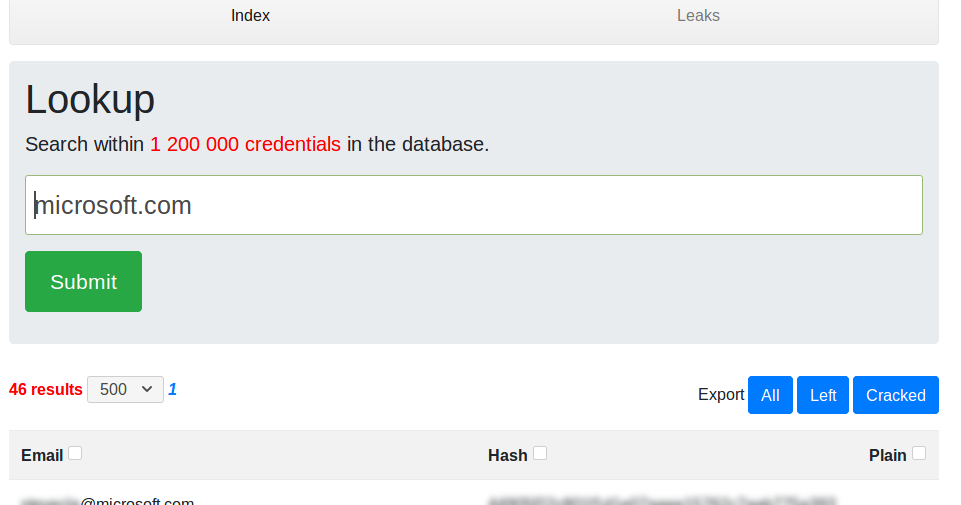
LeakScraper is an efficient set of tools to process and visualize huge text files containing credentials. These tools are designed to help...
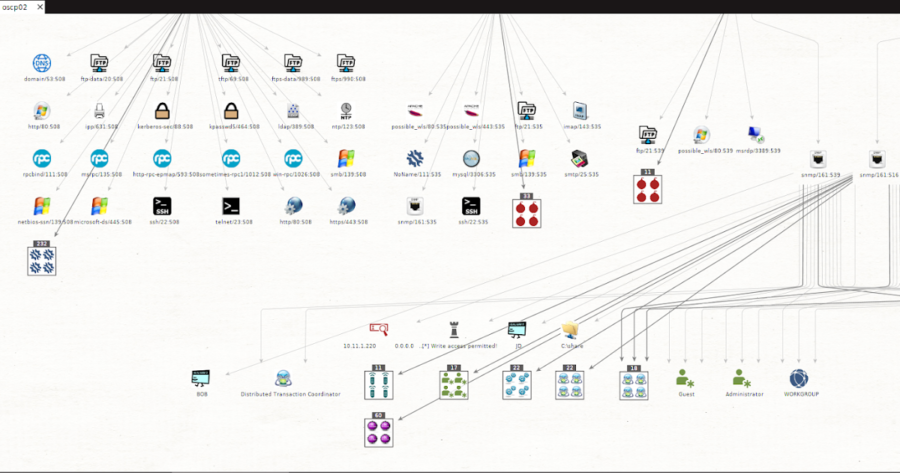
msploitego leverages the data gathered in a Metasploit database by enumerating and creating specific entities for services. Services like samba, smtp, snmp...
operative framework HD is the digital investigation framework, you can interact with websites, email address, company, people, ip address … with...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
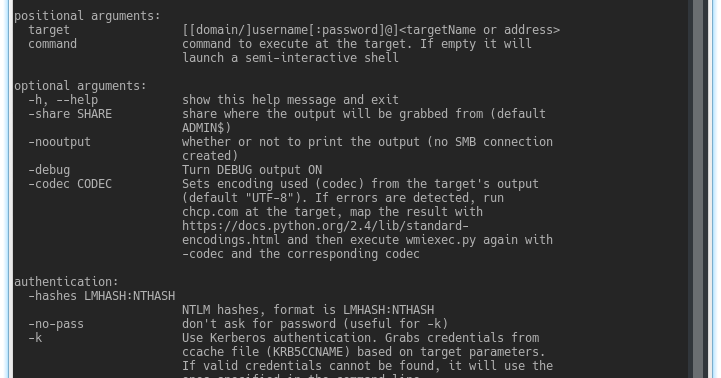
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
Hash Buster is a program which uses several APIs to perform hash lookups. Features Automatic hash type identification Supports MD5, SHA1, SHA2 Can extract...
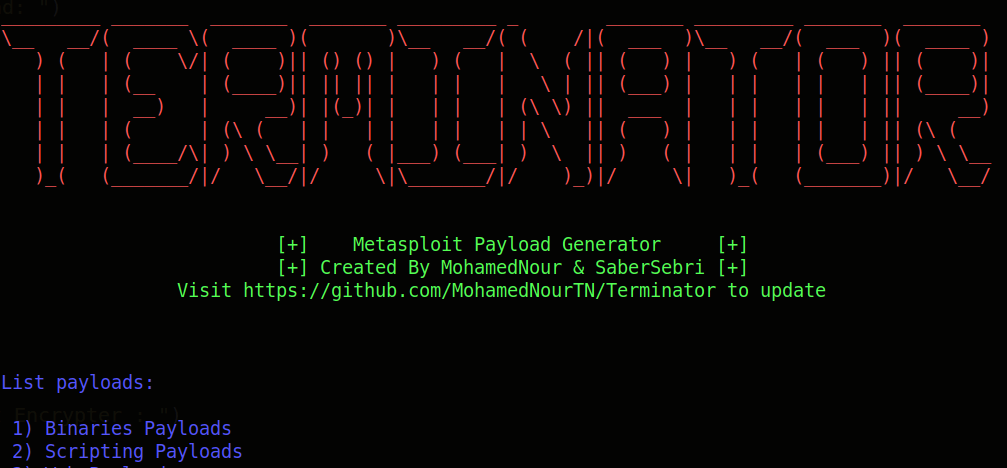
Terminator Metasploit Payload Generator. Payload List : Binaries Payloads 1) Android 2) Windows 3) Linux 4) Mac OS Scripting Payloads 1) Python 2) Perl 3) Bash...