[sc name=”ad_1″] “MEDUZA” (“медуза”) means “jellyfish” in Ukrainian What is MEDUZA? It’s a Frida...
Tag - iPhone
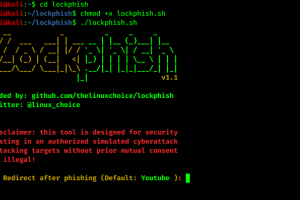
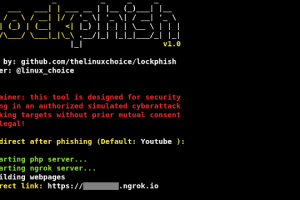
[sc name=”ad_1″] Lockphish it’s the first tool (07/04/2020) for phishing attacks on the lock screen, designed to grab Windows credentials...
[sc name=”ad_1″] Lockphish it’s the first tool (05/13/2020) for phishing attacks on the lock screen, designed to grab Windows credentials...
Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
This version of the application is written with Python programming language,which is used to crack the Restriction PassCode of iphone/ipad. Brute Force Get the...
Los Angeles natives Stefan Bogdanovich and Dakota Speas, represented by Wilshire Law Firm, this firm honed a lawsuit with the U.S. District Court for the...
After rapidly reinforcing a flaw that acknowledged anyone with access to a High Sierra Mac to take administrative control, Apple still has extra work to do to...
The group, called Google You Owe Us, said in a declaration Thursday that it was the first case of its sort in the U.K. against a major tech business over the...
Apple uses the Tenth Anniversary iPhone X Phone to replace Touch ID. Because the award handset features an edge-to-edge protection and has very slim bezels...