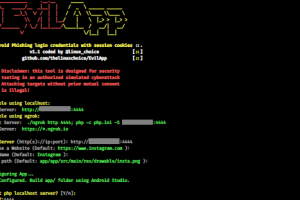
[sc name=”ad_1″] Man-in-the-middle phishing attack using an Android app to grab session cookies for any website, which in turn allows to bypass 2...
Tag - Bypass
[sc name=”ad_1″] A list of useful payloads and bypasses for Web Application Security. Feel free to improve with your payloads and techniques ...
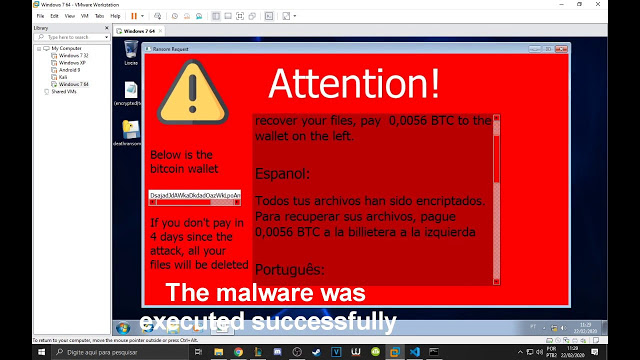
[sc name=”ad_1″] What is a ransomware? A ransomware is malware that encrypts all your files and shows a ransom request, which tells you to pay a...
[sc name=”ad_1″] Dolos Cloak is a python script designed to help network penetration testers and red teamers bypass 802.1x solutions by using an...
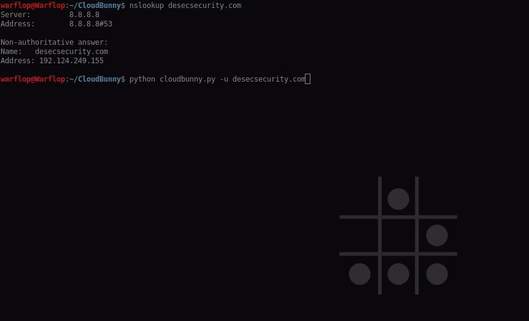
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
Author: Colin Harper If you’ve ever dealt in Bitcoin, you may have suffered through hour-long (or at worst, day-long) transaction times. It’s becoming...
Author: Alex Moskov What is Litecoin? Litecoin (LTC) is a decentralized peer-to-peer cryptocurrency that was released on October 7th, 2011 and went live on...
HatCloud is built in Ruby. It tries to bypass CloudFlare and discover real IP. This can be useful if you need to test your web server and website. HatCloud...
Author: Erin Gorsline The move marks the first time a Japanese Bank will launch a cryptocurrency and exchange. Worth more than financial mega-giant Bank of...
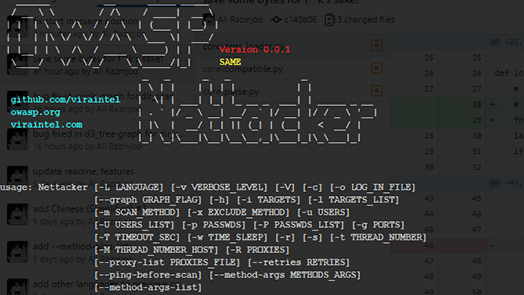
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...