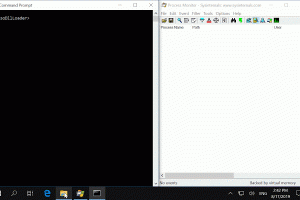
[sc name=”ad_1″] 2020-06-06 Update: this trick no longer works on the latest builds of Windows 10 Insider Preview. This means that, although it...
Search Results For - vulnerabilities
[sc name=”ad_1″] What is cross-site scripting (XSS)? Cross-site scripting (also known as XSS) is a web security vulnerability that allows an...
[sc name=”ad_1″] Spyse is a cybersecurity search engine for finding technical information about different internet entities, business data, and...
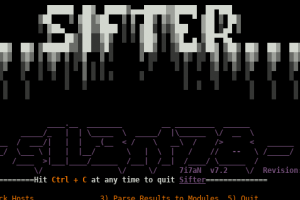
[sc name=”ad_1″] Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to...
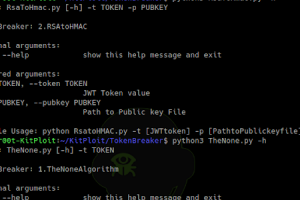
[sc name=”ad_1″] Token Breaker is focused on 2 particular vulnerability related to JWT tokens. None Algorithm RSAtoHMAC Refer to this link about...
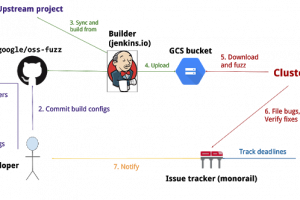
[sc name=”ad_1″] Fuzz testing is a well-known technique for uncovering programming errors in software. Many of these detectable errors, like buffer...
[sc name=”ad_1″] The script aims to help in classifying vulnerabilities in web applications. The methodology RecoX is arising can spot weaknesses...
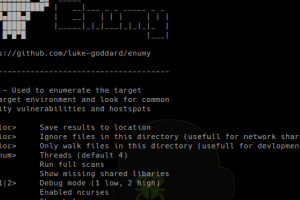
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
[sc name=”ad_1″] All-in-one tool for managing vulnerability reports Why The goal of Purify to be an easy-in-use and efficient tool to simplify a...
[sc name=”ad_1″] Working and learning have gone remote, and we have to come to terms with this new reality. Nowadays, several organizations allow...