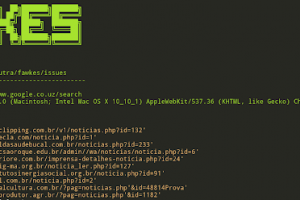
[sc name=”ad_1″] Fawkes is a tool to search for targets vulnerable to SQL Injection. Performs the search using Google search engine. Options...
Search Results For - Vulnerable
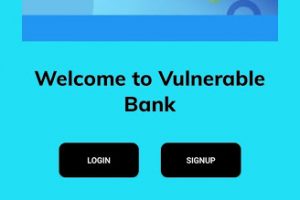
[sc name=”ad_1″] Damn Vulnerable Bank Android Application aims to provide an interface for everyone to get a detailed understanding with internals...
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...
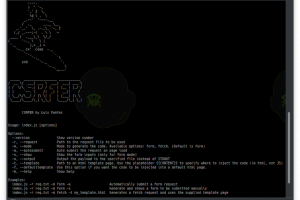
[sc name=”ad_1″] CSRFER is a tool to generate csrf payloads, based on vulnerable requests. It parses supplied requests to generate either a form or...
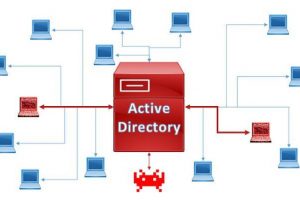
[sc name=”ad_1″] Create a vulnerable active directory that’s allowing you to test most of active directory attacks in local lab. Main...
[sc name=”ad_1″] Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url=...
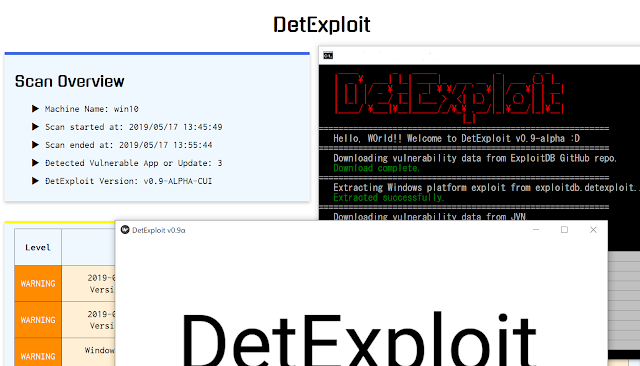
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
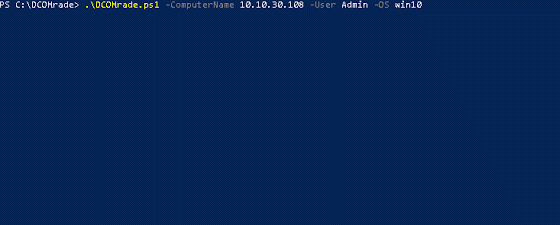
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...
[sc name=”ad_1″] Smart devices definitely make our lives easier, faster, and more efficient, but unfortunately, an insecure smart device can also...
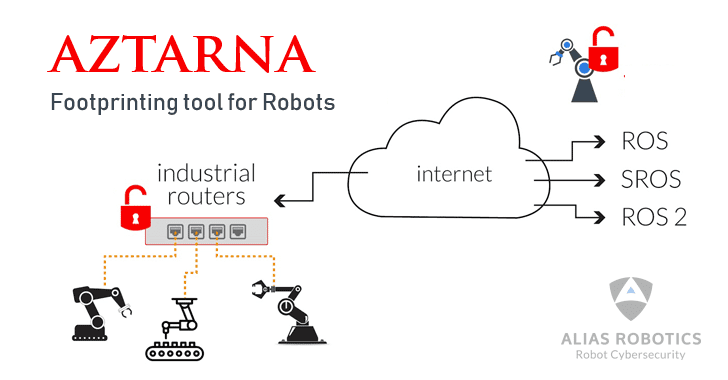
[sc name=”ad_1″] A team at a robot cybersecurity startup has released a free, open-source tool for information security professionals to help them...