The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over...
Search Results For - Vulnerable
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...
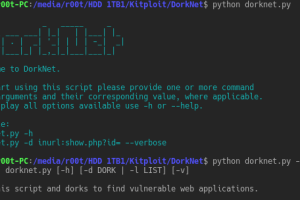
Selenium powered Python script to automate searching the web for vulnerable applications. DorkNet can take a single dork or a list of dorks as arguments. After...
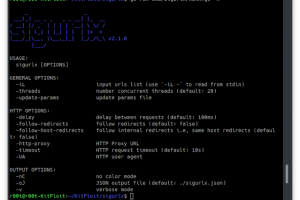
[sc name=”ad_1″] sigurlx a web application attack surface mapping tool, it does …: Categorize URLs URLs’ categories: > endpoint >...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
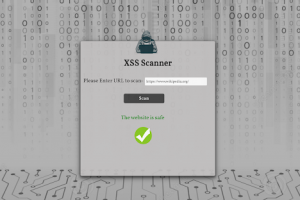
[sc name=”ad_1″] Cross-Site Scripting (XSS) is one of the most well known web application vulnerabilities. It even has a dedicated chapter in the...
[sc name=”ad_1″] Aura is a static analysis framework developed as a response to the ever-increasing threat of malicious packages and vulnerable...
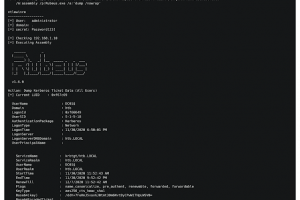
[sc name=”ad_1″] A sharpen version of CrackMapExec. This tool is made to simplify penetration testing of networks and to create a swiss army knife...
[sc name=”ad_1″] Automated Web Assets Enumeration & Scanning Instructions for running Create an account on Zulip Navigate to...
[sc name=”ad_1″] Project Bheem is a simple collection of small bash-scripts which runs iteratively to carry out various tools and recon process...