[sc name=”ad_1″] Safety checks your installed dependencies for known security vulnerabilities. By default it uses the open Python vulnerability...
Search Results For - Vulnerability
[sc name=”ad_1″] For the most up-to-date information on Anchore Engine, Anchore CLI, and other Anchore software, please refer to the Anchore...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
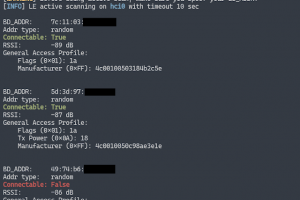
[sc name=”ad_1″] Bluescan is a open source project by Sourcell Xu from DBAPP Security HatLab. Anyone may redistribute copies of bluescan to anyone...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
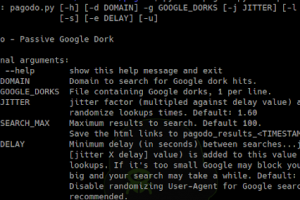
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
[sc name=”ad_1″] EternalBlue suite remade in C which includes: MS17-010 Exploit, EternalBlue/MS17-010 vulnerability detector, DoublePulsar detector...
[sc name=”ad_1″] A tool that detects the privilege escalation vulnerabilities caused by misconfigurations and missing updates in the Windows...