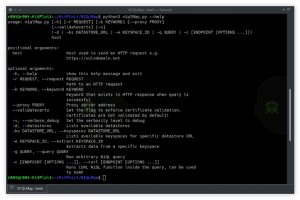
[sc name=”ad_1″] N1QLMap is an N1QL exploitation tool. Currently works with Couchbase database. The tool supports data extraction and performing...
Search Results For - Vulnerability
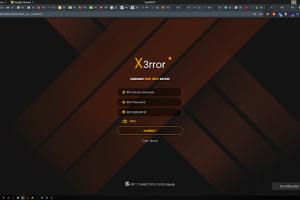
[sc name=”ad_1″] Xerror is an automated penetration tool , which will helps security professionals and non professionals to automate their...
[sc name=”ad_1″] A (coverage-)guided fuzzer for dynamic language interpreters based on a custom intermediate language (“FuzzIL”) which...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
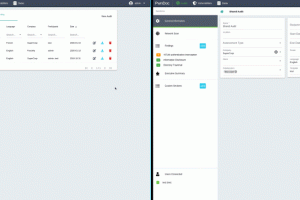
[sc name=”ad_1″] PwnDoc is a pentest reporting application making it simple and easy to write your findings and generate a customizable Docx report...
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...
[sc name=”ad_1″] As indicated by sources like vulndb & cve, on a daily basis, approximately 50 new vulnerabilities become known to industry and...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
[sc name=”ad_1″] Welcome to the Microsoft Defender Advanced Threat Protection PowerShell module! This module is a collection of easy-to-use cmdlets...