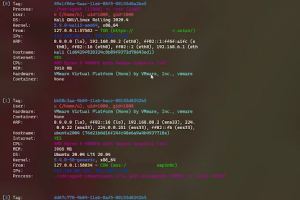
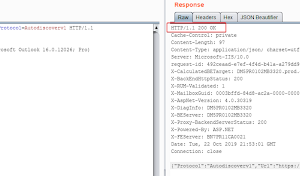
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
Search Results For - Vulnerability
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] This cli is for pentesters, CTF players, or dev. You can modify your jwt, sign, inject ,etc… Check Documentation for more...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] A script that can see if an email address is valid in Office365. This does not perform any login attempts, is unthrottled, and is...
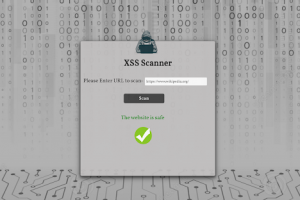
[sc name=”ad_1″] Cross-Site Scripting (XSS) is one of the most well known web application vulnerabilities. It even has a dedicated chapter in the...
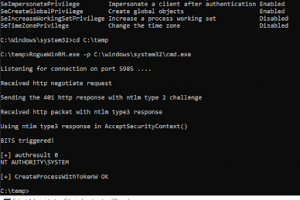
[sc name=”ad_1″] RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with SeImpersonatePrivilege) to...
[sc name=”ad_1″] Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your...
[sc name=”ad_1″] A small contribution to community 🙂 We use all these tools in security assessments and in our vulnerability monitoring service...